Cyber Security News
@The_Cyber_News
Independent Cyber Security News Platform For Security Professionals to Get the Latest #HackingNews, #CyberCrime, #SecurityBreaches, #Malware & Others...
ID:1165106855879704577
http://www.cybersecuritynews.com 24-08-2019 03:41:46
4,2K Tweets
4,9K Followers
218 Following

🚨 Hackers Compromised SOHO 600,000 Routers Within 72 Hours For Botnet Cyber Security News
Learn more: cybersecuritynews.com/hackers-compro…
Hackers often target the routers to take charge of network traffic, get hold of sensitive data, and attack attached devices.
#cybersecuritynews #malware

Beware of Fake Browser Updates That Deliver Bitrat & Lumma Stealer Cyber Security News
The attackers use fake update mechanisms to trick users into downloading malicious files, leading to severe security breaches.
Learn more: gbhackers.com/beware-of-fake…
#cybersecuritynews

RedTail Cryptominer Exploiting Palo Alto Networks Firewall Zero-day Flaw Cyber Security News
Learn more: cybersecuritynews.com/redtail-miner-…
RedTail cryptocurrency mining malware has been observed exploiting a critical zero-day vulnerability in Palo Alto Networks’ firewall software, PAN-OS.

BBC Data Breach: Hackers Access Cloud-Based Storage Service @the_cyber_news
Learn more: cybersecuritynews.com/bbc-data-breac…
The BBC has confirmed a data security incident involving the personal information of some members of the BBC Pension Scheme.
#cybersecuritynews #databreach

New Meterpreter Backdoor Hides Malicious Codes Within the Image Cyber Security News
Learn more: cybersecuritynews.com/meterpreter-ba…
ANY RUN sandbox has analyzed a new strain of Meterpreter backdoor malware that leverages sophisticated steganography techniques to conceal its malicious payload

Operation Endgame: Authorities Seized IcedID, Pikabot, & Other Droppers Cyber Security News
Learn more: cybersecuritynews.com/operation-endg…
Operation Endgame, led by Europol, targeted a range of malicious software droppers, including IcedID, SystemBC, Pikabot, Smokeloader, Bumblebee, and

🚨 Okta Warns Credential Stuffing Attacks Targeting Customer Identity Cloud Cyber Security News
The company has identified threat actors exploiting the cross-origin authentication feature within CIC.
Learn more: gbhackers.com/okta-warns-stu…
#cybersecuritynews #okta

Indian Stock Exchange BSE Starts Encrypting Messages to Traders Cyber Security News
Learn more: cybersecuritynews.com/bse-starts-enc…
The Bombay Stock Exchange (BSE) has begun encrypting messages sent to traders, becoming the first exchange in the world to implement such a system.

🚨 Phishing with Cloudflare Workers: Transparent Phishing and HTML Smuggling Cyber Security News
Learn more: gbhackers.com/phishing-with-…
Phishing campaigns are abusing Cloudflare workers in two ways, where one injects malicious content hidden by HTML smuggling, similar to Azorult


🛡 Check Point VPN Zero-Day Vulnerability Exploited in Wild to Gain Remote Access Cyber Security News
Learn more: cybersecuritynews.com/check-point-vp…
The vulnerability, tracked as CVE-2024-24919, allows attackers to gain unauthorized access to sensitive information on internet-connected

🚨DATA BREACH🚨A threat actor claims to have extracted more than 200 million recent records from Facebook and Instagram.
#DarkWeb #Cybersecurity #Security #Cyberattack #Cybercrime #Privacy #Infosec
Compromised Data: Name, Email, Phone number, UID, Username, Location, Cities,


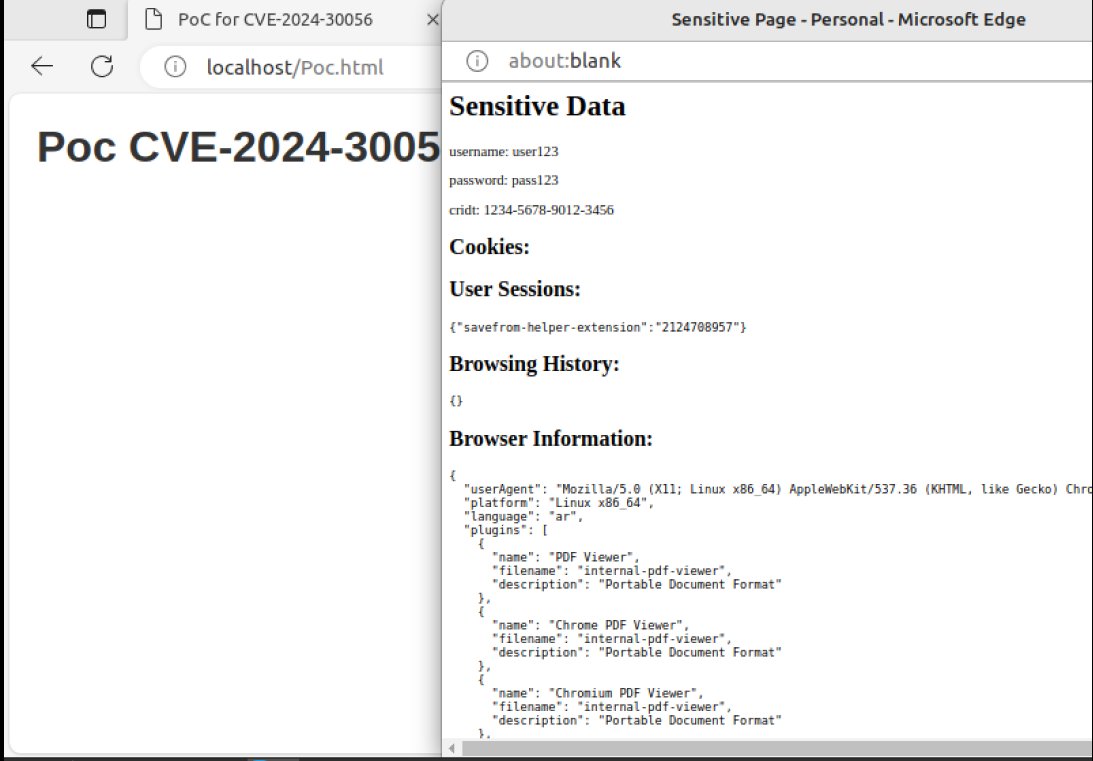
🚨POC RELEASED🚨CVE-2024-30056 Microsoft Edge (Chromium-based) Information Disclosure Vulnerability
#DarkWeb #Cybersecurity #Security #Cyberattack #Cybercrime #Privacy #Infosec #CVE202430056 #Vulnerability
This is a vulnerability in Microsoft Edge (Chromium-based). The attacker

Seattle Public Library Website offline Following Ransomware Attack Cyber Security News
Seattle Public Library (SPL) experienced a ransomware attack that significantly disrupted its technology systems.
Learn more: cybersecuritynews.com/seattle-librar…
#cybersecuritynews #ransomware

PoC Exploit Released for Critical Fortinet FortiSIEM Command Injection Vulnerability Cyber Security News
Learn more: cybersecuritynews.com/poc-exploit-fo…
The vulnerability, CVE-2024-23108, allows for remote, unauthenticated command execution as root.
#cybersecuritynews

CatDDoS Exploiting 80+ Vulnerabilities, Attacking 300+ Targets Daily Cyber Security News
Learn more: gbhackers.com/catddos-ddos-a…
Malicious traffic floods targeted systems, servers, or networks in Distributed Denial of Service (DDoS) attacks are actively exploited by hackers.

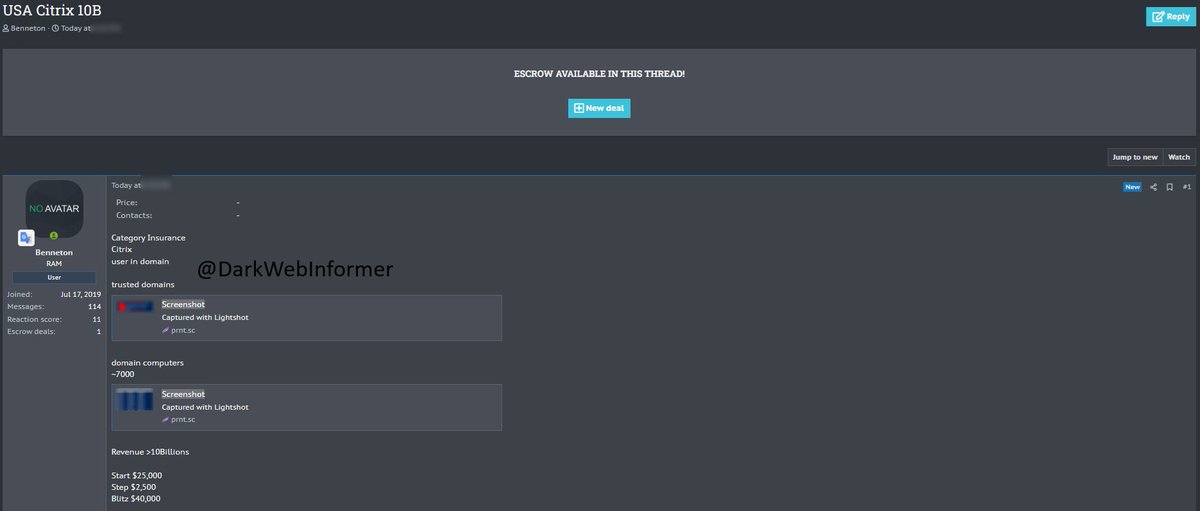
🚨Access For Sale🇺🇸🚨A threat actor is allegedly selling Citrix access to an unknown $10 Billion company in the Insurance industry. Start: $25,000. Step: $2,500. Blitz: $40,000.
#DarkWeb #Cybersecurity #Security #Cyberattack #Cybercrime #Privacy #Infosec

Zscaler Client Connector Zero-interaction Privilege Escalation Vulnerability Cyber Security News
Learn more: cybersecuritynews.com/zscaler-client…
A new privilege escalation vulnerability has been discovered in Zscaler Client Connector, combining three different vulnerabilities.

Researchers Detailed Modern WAF Bypass Techniques With Burp Suite Plugin Cyber Security News
Learn more: cybersecuritynews.com/waf-bypass-usi…
Security experts have disclosed advanced methods for bypassing Web Application Firewalls (WAFs) on a large scale and introduced a new Burp Suite plugin

🚨 Hackers Exploiting Arc Browser Popularity with Malicious Google Search Ads Cyber Security News
Learn more: cybersecuritynews.com/hackers-exploi…
The ad campaign impersonates the Arc browser, which looks entirely legitimate with the official logo and website.
#cybersecuritynews #googleads