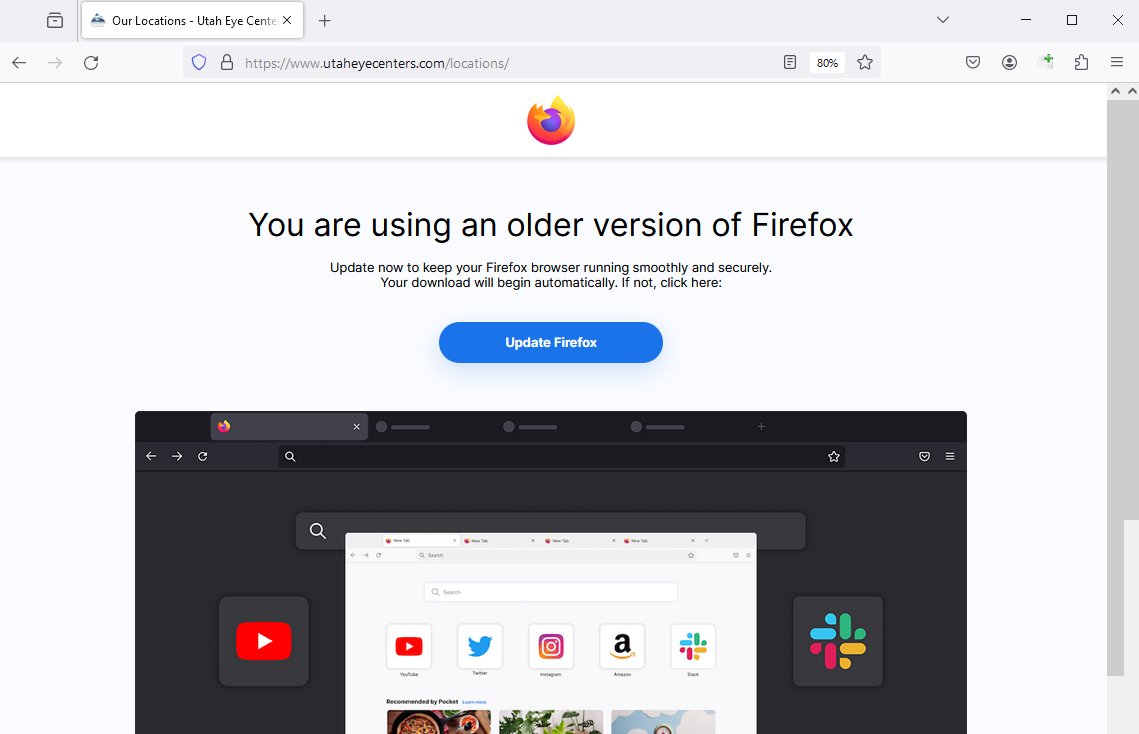
Usage of fake browser update is the new technique to attack the other devices.
For such more updates, follow @Seninjaz_tech
#cybersecurity #NetSupportrat #trojan #security #cybercrime #weekulyupdates #secninjaztechnologies

Observed #NetSupportRAT
➡️js Browser_update16.0.5836.js->DLs and exec 11.bat from magydostravel[.]com
➡️11.bat->DLs lolo.7z,7zip,22.bat from mangoairsoft[.]com
➡️lolo.7z->NetSupportRAT-> C2: 94.158.247[.]23:5050
➡️22.bat->persistence regkey->netsupporRAT
![x3ph (@x3ph1) on Twitter photo 2023-08-02 01:46:43 Observed #NetSupportRAT
➡️js Browser_update16.0.5836.js->DLs and exec 11.bat from magydostravel[.]com
➡️11.bat->DLs lolo.7z,7zip,22.bat from mangoairsoft[.]com
➡️lolo.7z->NetSupportRAT-> C2: 94.158.247[.]23:5050
➡️22.bat->persistence regkey->netsupporRAT Observed #NetSupportRAT
➡️js Browser_update16.0.5836.js->DLs and exec 11.bat from magydostravel[.]com
➡️11.bat->DLs lolo.7z,7zip,22.bat from mangoairsoft[.]com
➡️lolo.7z->NetSupportRAT-> C2: 94.158.247[.]23:5050
➡️22.bat->persistence regkey->netsupporRAT](https://pbs.twimg.com/media/F2fX6XQXEAANsA_.png)

I am naming this #RogueRaticate campaign that leverages URL shortcuts to drop #NetSupportRAT 🐀
1/
➡️ The user is getting infected via a drive-by download with the fake update screen (similar to SocGholish behavior). The initial payload is hosted on compromised WordPress


1/ #SocGholish #FakeUpdates 👻
Similar to the previous infection x.com/anfam17/status…
Download URL: publicccescpolace[.]com
NetSupportRAT C2: 94.158.244[.]118:1203
![RussianPanda 🐼 🇺🇦 (@RussianPanda9xx) on Twitter photo 2023-02-24 05:49:01 1/ #SocGholish #FakeUpdates 👻
Similar to the previous infection x.com/anfam17/status…
Download URL: publicccescpolace[.]com
NetSupportRAT C2: 94.158.244[.]118:1203 1/ #SocGholish #FakeUpdates 👻
Similar to the previous infection x.com/anfam17/status…
Download URL: publicccescpolace[.]com
NetSupportRAT C2: 94.158.244[.]118:1203](https://pbs.twimg.com/media/FptaZB-X0AEdHE7.png)

Observed #netsupportrat
➡️Compressed gzip file containing a javascript called date_browser_176436.js
➡️JS->writes a compressed zip named 'Update - 920240108\.zip' file containing 3 javascript files->JS->DLs VBS from https[:]//choosetotruck[.]com/cache/letter.php->loads PS
![x3ph (@x3ph1) on Twitter photo 2024-01-09 18:21:01 Observed #netsupportrat
➡️Compressed gzip file containing a javascript called date_browser_176436.js
➡️JS->writes a compressed zip named 'Update - 920240108\.zip' file containing 3 javascript files->JS->DLs VBS from https[:]//choosetotruck[.]com/cache/letter.php->loads PS Observed #netsupportrat
➡️Compressed gzip file containing a javascript called date_browser_176436.js
➡️JS->writes a compressed zip named 'Update - 920240108\.zip' file containing 3 javascript files->JS->DLs VBS from https[:]//choosetotruck[.]com/cache/letter.php->loads PS](https://pbs.twimg.com/media/GDa34yUWgAEJJzr.png)

#SOCGholish observed
➡️FakeBrowserUpdate downloads and runs on system.
➡️Implant of NetSupportRAT
➡️NetSupportRAT established connections: noinmsyvhruhjbi4hs[.]cn, gkdkr[.]icu
![x3ph (@x3ph1) on Twitter photo 2023-01-09 22:52:36 #SOCGholish observed
➡️FakeBrowserUpdate downloads and runs on system.
➡️Implant of NetSupportRAT
➡️NetSupportRAT established connections: noinmsyvhruhjbi4hs[.]cn, gkdkr[.]icu #SOCGholish observed
➡️FakeBrowserUpdate downloads and runs on system.
➡️Implant of NetSupportRAT
➡️NetSupportRAT established connections: noinmsyvhruhjbi4hs[.]cn, gkdkr[.]icu](https://pbs.twimg.com/media/FmEINn4WYAEzf2d.png)

Beware: FIN7 hacker group's latest tactic involves using malicious Google Ads to distribute NetSupport RAT.
Stay vigilant and ensure robust cybersecurity measures!
#FIN7 #CyberSecurity #NetSupportRAT

1/ #socgholish deploying #NetSupportRAT at the first stage. The threat actor(s) deployed a PowerShell script via the NetSupport session after 2 days. Thanks dr4k0nia for a reversing session, she found the next stage to be #asyncrat 🐀
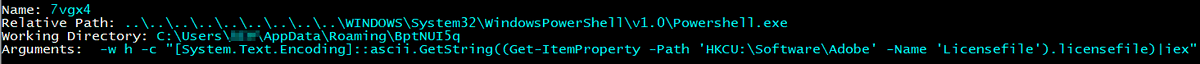

Protect your organization from phishing with NetSupport RAT, cloud platform abuse for undetectable URLs, and hackers targeting Windows NTLM hashes. Get our comprehensive guide now - wati.com/guide-to-prote…
#PhishingEmails #NetSupportRAT #CloudSecurity #WATICybersecurity


1/ #socgholish is this you? 👻
➡️UpdateInstaller.zip > Update.js
➡️Retrieves #NetSupportRAT 🐀 and batch scripts from C2
🖥️C2 IP: 188.127.231[.]11
eSentire Threat Intel
![RussianPanda 🐼 🇺🇦 (@RussianPanda9xx) on Twitter photo 2023-02-09 22:07:05 1/ #socgholish is this you? 👻
➡️UpdateInstaller.zip > Update.js
➡️Retrieves #NetSupportRAT 🐀 and batch scripts from C2
🖥️C2 IP: 188.127.231[.]11
@esthreat 1/ #socgholish is this you? 👻
➡️UpdateInstaller.zip > Update.js
➡️Retrieves #NetSupportRAT 🐀 and batch scripts from C2
🖥️C2 IP: 188.127.231[.]11
@esthreat](https://pbs.twimg.com/media/FojqqcNXgAEB50C.png)

🐀 #NetSupportRAT might look harmless, but criminals love this tool - use these #KQL queries to check your environment for signs of compromise! 🕵️ github.com/reversinglabs/…
#malware #infosec #informationsecurity #cybersecurity #threatintel #threatintel ligence #microsoftsentinel



#socgholish #NetSupportRat
SocGholish Stage1 - taxes.rpacx[.]com
SocGholish Stage2 - hjgk67kg[.]xyz
SocGholish Stage3 - *.asset.tradingvein[.]xyz
NetSupportRat C2 - 52226asdiobioboioie[.]com (IP 94.158.244.38)
![Broad Analysis (@BroadAnalysis) on Twitter photo 2023-01-11 19:23:20 #socgholish #NetSupportRat
SocGholish Stage1 - taxes.rpacx[.]com
SocGholish Stage2 - hjgk67kg[.]xyz
SocGholish Stage3 - *.asset.tradingvein[.]xyz
NetSupportRat C2 - 52226asdiobioboioie[.]com (IP 94.158.244.38) #socgholish #NetSupportRat
SocGholish Stage1 - taxes.rpacx[.]com
SocGholish Stage2 - hjgk67kg[.]xyz
SocGholish Stage3 - *.asset.tradingvein[.]xyz
NetSupportRat C2 - 52226asdiobioboioie[.]com (IP 94.158.244.38)](https://pbs.twimg.com/media/FmNux0dWIA4L_ff.jpg)

Observed #NetSupportRAT
A new domain has been observed trk.canadiantrk[.]site, leading to a download of Version2.exe which installs an instance of transmission-qt which then implants NetSupportRAT, C2 206.166.251[.]123.
CC Gi7w0rm, Namecheap.com
![x3ph (@x3ph1) on Twitter photo 2023-06-10 14:54:45 Observed #NetSupportRAT
A new domain has been observed trk.canadiantrk[.]site, leading to a download of Version2.exe which installs an instance of transmission-qt which then implants NetSupportRAT, C2 206.166.251[.]123.
CC @Gi7w0rm, @Namecheap Observed #NetSupportRAT
A new domain has been observed trk.canadiantrk[.]site, leading to a download of Version2.exe which installs an instance of transmission-qt which then implants NetSupportRAT, C2 206.166.251[.]123.
CC @Gi7w0rm, @Namecheap](https://pbs.twimg.com/media/FyRQE8SWcAAUioS.png)

Other commodity #malware used by the group comprises a combination of remote access #trojans & information stealers such as #AsyncRAT , #NetSupportRAT , & #Rhadamanthys .
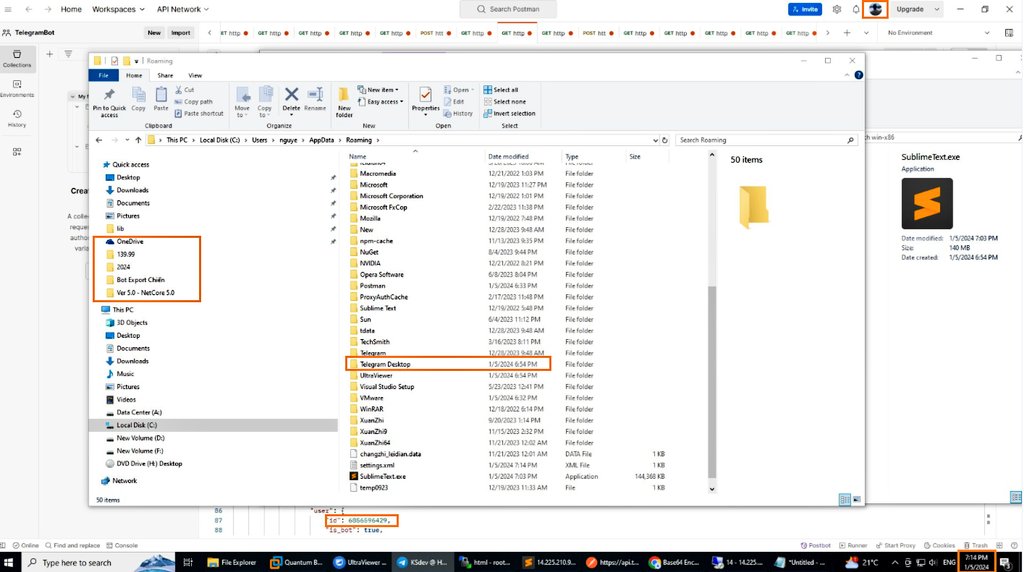


Beware of the new #CyberThreat — the remote access trojan, NetSupportRAT.
Through fraudulent updates, malware and phishing, criminals are hacking into victims’ computers and networks...
To protect your business, call our team of #CyberSecurity specialists on 01252 843014.



1/
Two-in-one: Wallet drainer & #NetSupportRAT
Mass mentions & DMs to lure -> Pokemon Stacking Cards Game (82226526)
/pokemoncards-nft.com
Notif to: 195.133.197[.]185
🚩Etherscan
0xaAcCa4Ed989A3508d37e2432ADE900B8Ce657d2F
has back-and-forth txs: 0xE497Dc4cDCCbE258968A65dEBbe2006d3B3Ad15f
![iamdeadlyz (@Iamdeadlyz) on Twitter photo 2023-02-16 18:24:30 1/
Two-in-one: Wallet drainer & #NetSupportRAT
Mass mentions & DMs to lure -> @jobjobsjob (82226526)
/pokemoncards-nft.com
Notif to: 195.133.197[.]185
🚩@etherscan
0xaAcCa4Ed989A3508d37e2432ADE900B8Ce657d2F
has back-and-forth txs: 0xE497Dc4cDCCbE258968A65dEBbe2006d3B3Ad15f 1/
Two-in-one: Wallet drainer & #NetSupportRAT
Mass mentions & DMs to lure -> @jobjobsjob (82226526)
/pokemoncards-nft.com
Notif to: 195.133.197[.]185
🚩@etherscan
0xaAcCa4Ed989A3508d37e2432ADE900B8Ce657d2F
has back-and-forth txs: 0xE497Dc4cDCCbE258968A65dEBbe2006d3B3Ad15f](https://pbs.twimg.com/media/FpGryn0aYAAxGHt.png)