We'll be at Open Source Summit North America!
#opensourcesoftware #SoftwareSupplyChain #CyberSecurity #OpenSource Security #SecureCoding #Sigstore #OpenSource #DeveloperCommunity



🌟 Catch Thomas Vitale Thomas Vitale at DEVOXX UK this Wed! Dive into software supply chain security with live demos. 📅 May 8, Room A
📚 Learn more: mng.bz/oeoj
#DEVOXXUK #Java #ManningBooks #softwaresupplychain

Get ready, Open Source Summit North America attendees! Don't miss Craig McLuckie's keynote speech on the 17th at 10:20 AM PST! See details and add it to your schedule here: hubs.la/Q02sBzml0
#SoftwareSupplyChain #OpenSource Security #Sigstore #OpenSource #DeveloperCommunity


Kubernetes Community Days Istanbul 2023
#redhat #secure #softwaresupplychain #kubernetes
red.ht/trusted

🌐 tea Protocol : a decentralized protocol securing the software supply chain, boosting sustainability, and integrity. It enables open-source developers to capture the value they create in a trustless manner. #DecentralizedProtocol #SoftwareSupplyChain #OpenSourceDevelopment

Attend SecureChainCon and learn about #in -toto and #OPA Gatekeeper from John Kjell at TestifySec. Security in the pipeline is critical, #SecureChainCon digs in. #softwaresupplychain #cybersecurity #devops #devsecops Learn More at ortelius.io/blog/2024/02/2…


Let's get Øredev started.
My first session out or 4 on Software Supply Chain Security starts at 11 in Nova
#slsa #softwaresupplychain #softwaresecurity


Ive just published 'Securing the Supply Chain of Containerized Applications to Reduce Security Risks (Security Scanning,SBOMs,Signing&Verifying Artifacts) –Part1'
EN: gokhan-gokalp.com/en/securing-th…
TR: cozumpark.com/containerized-…
#softwaresupplychain #container #security #sbom #devsecops


Are you ready to take your defense against supply chain attacks to the next level? Join Jim Manico from Manicode Security, @JavaJulius & S Smith tomorrow for this exciting webinar on WAF & Runtime Protection!
Register: mergebase.com/waf-vs-java-ru…
#waf #runtimeprotection #softwaresupplychain


Sam Stewart, Co-Founder and CEO of Ensignia, will join us at #HardlyStrictlySecurity to digest the current state of #SoftwareSupplyChain #security and leave with a recipe for building a healthier ecosystem—one link at a time. Don’t miss this and join us for free.

More threats against #OpenSource #software could be coming soon, experts warn - buff.ly/3JiJrLZ #security #software supplychain #JavaScript #security #cybersecurity


For anyone looking for a last minute Halloween Costume... We hear that supply chain security experts get paid well... This kit could get you started. 😎 💻
Stay safe out there in the digital world.
#halloween #cybersecurity #softwaresupplychain


Read our latest blog post to learn about the evolution of code signing and its crucial role in ensuring software authenticity and integrity.
ow.ly/yzgz50RzGe5
#CodeSign ing #CodeSign #SoftwareSecurity #CICD #CICD Pipeline #HSM #SoftwareSupplyChain #SupplyChainAttack


Join Jim Manico from Manicode Security , @JavaJulius & S Smith in this mini-webinar series on MergeBase’s patented Java Runtime Protection.
Starting next Tuesday, January 17th at 10 am PST.
Check more info and register: mergebase.com/runtime-webina…
#runtimeprotection #sca #softwaresupplychain


Attend SecureChainCon and learn about #GoogleCloud Software Supply Chain Security from Nael Fridhi, at Google Cloud. Security in the pipeline is critical, #SecureChainCon digs in. #softwaresupplychain #cybersecurity #devops #devsecops Learn More at ortelius.io/blog/2024/02/2…


📣 Miss our discussion on #SoftwareSupplyChain #Security ? Join Ed Warnicke, Michael Chenetz, æva black, Brandon Lum,Dan Lorenc, & Cole Kennedy
as they chat software supply chain. From historical mistakes to a single source of truth, we covered it!
On demand.📷 cs.co/6013OQaOz



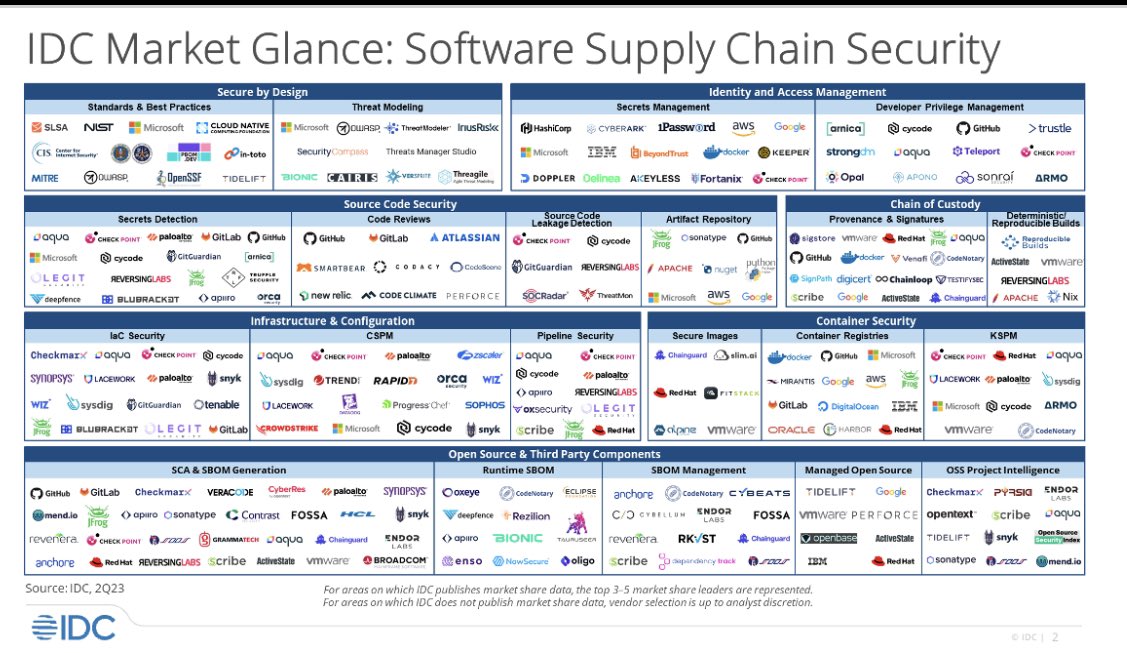
Excited to share Jim Mercer and my latest research - IDC’s first Software Supply Chain Security Market Glance - a high-level and illustrative graphical overview, laying out the key segments and identifying vendors that offer solutions in each. #softwaresupplychain

Addressing CVEs in Open Source can be a real challenge, especially when stakeholders aren't aligned. Learn how to reduce time, cost, and overhead in this blog post!
buff.ly/44P5Ecy
#Java #SoftwareSupplyChain #DevSecOps