With more than 65 trillion cybersecurity signals detected daily, how do we make sense of all this data? Learn how we use these insights to stop threats and power generative AI: msft.it/6013cQJ31 #CyberSignals #ThreatIntelligence

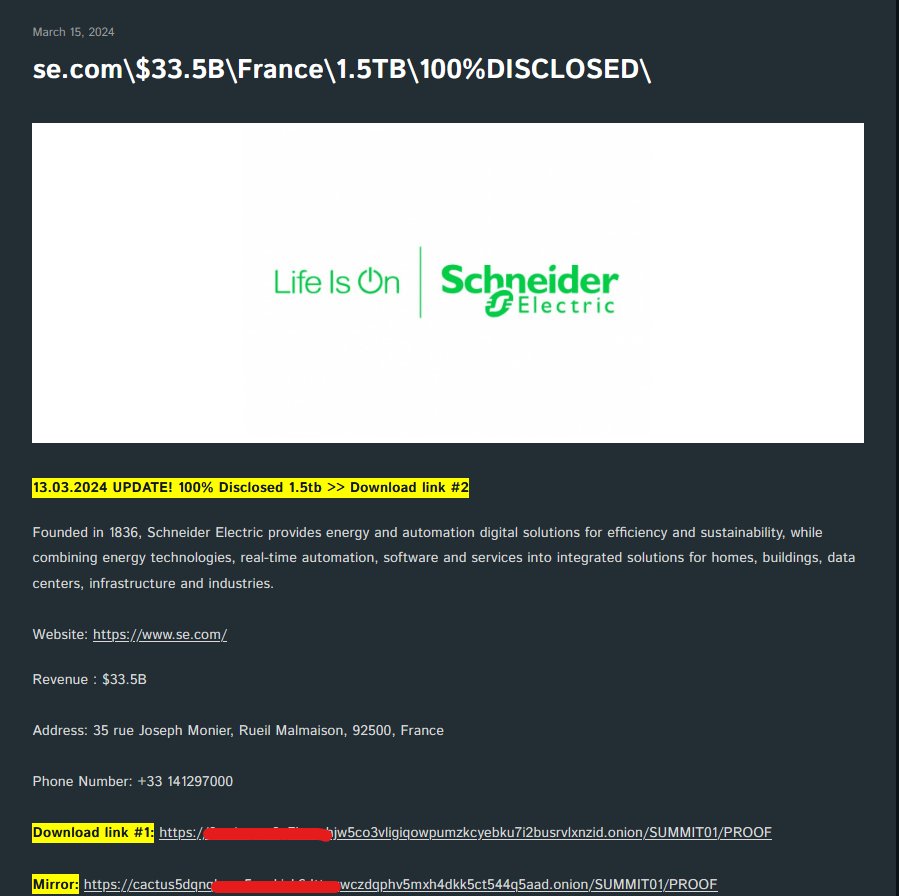
Schneider Electric'e ait 1.6 TB Data leak edildi. Cactus APT grubu daha önce kuruma sızdığını söylemişti. Fidye ödenmediği için Dataları leak ettiler. Habib Karataş
#SiberGüvenlik #leaked #threatintelligence #cybersecurity

🚨 #Workshop 🔍 Do you know Advanced Techniques for Detecting New Malicious Infrastructure ?
🕵️Zach Edwards ( Zach Edwards ) from Silent Push will conduct workshop on Unveiling Sophisticated Threat Actors 🦹♂️ at #PIVOTcon24 day 0
#CTI #ThreatIntelligence
1/5


You just got 45 more pages of #threatintelligence . Enter Prelude's new set of autonomous capabilities—built to transform that CTI into validated protections...fast.
See how we're leveraging AI to unify SecOps and streamline the threat management process: hubs.la/Q02vS-pF0

Threat actors know how to manipulate emotions. Making you feel fearful, guilty, or angry can give cyberattackers an upper hand—learn how: msft.it/6014cfhl8 #ThreatIntelligence #SecurityInsider

👋 Welcome our new team members!
Thank you for being part of our team! We look forward to achieving great things together 🤝
#OpenCTI #OpenBAS #OpenSource #Cybersecurity #ThreatIntelligence #Software


🚀 Just wrapped up an incredible technical talk by Aditya K Sood on 'Striking C&C Infrastructure for Generating Applied Threat Intelligence' at #BSidesGoa 2024 ! 💡
#CybersecurityTalks #ThreatIntelligence #BSidesGoa 🌐🔒



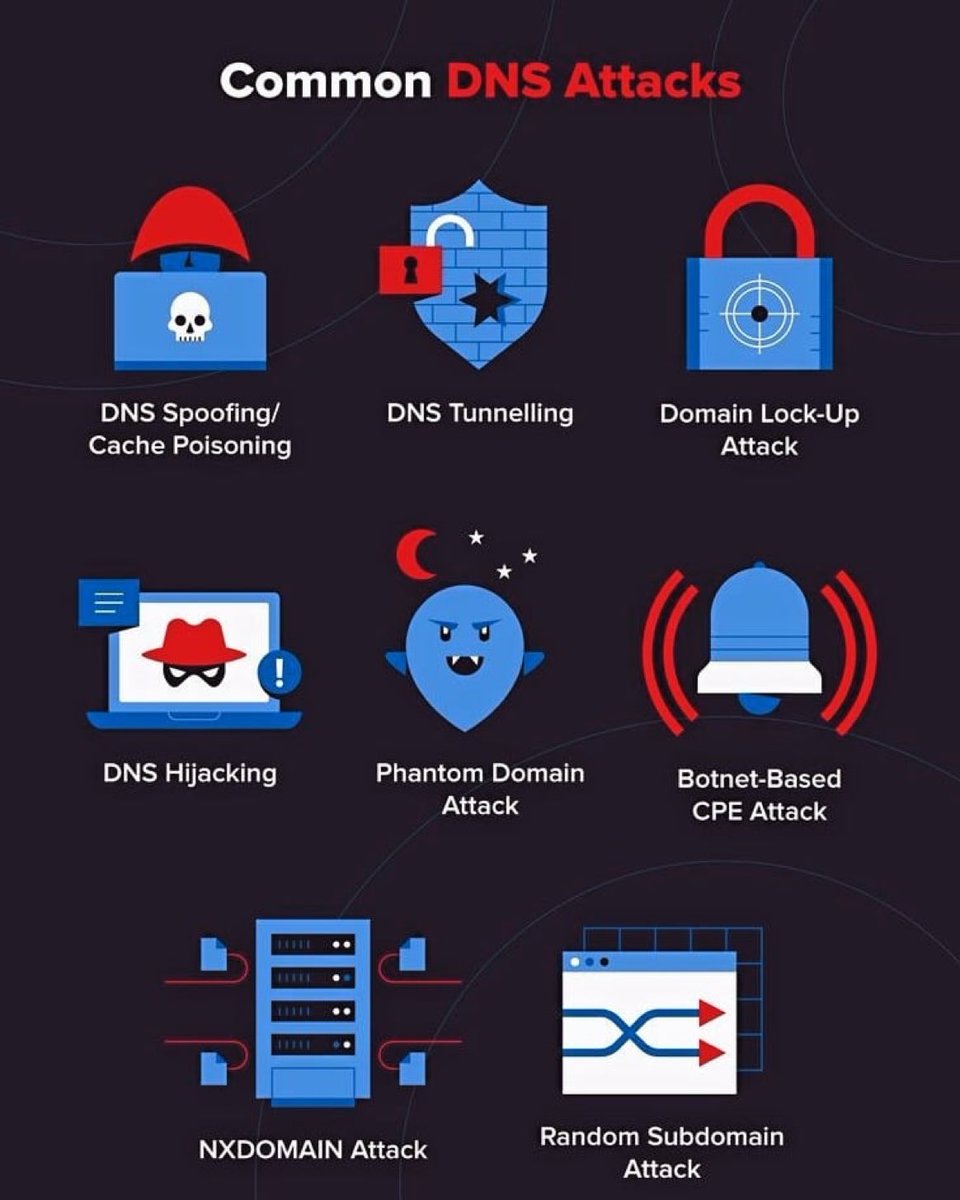
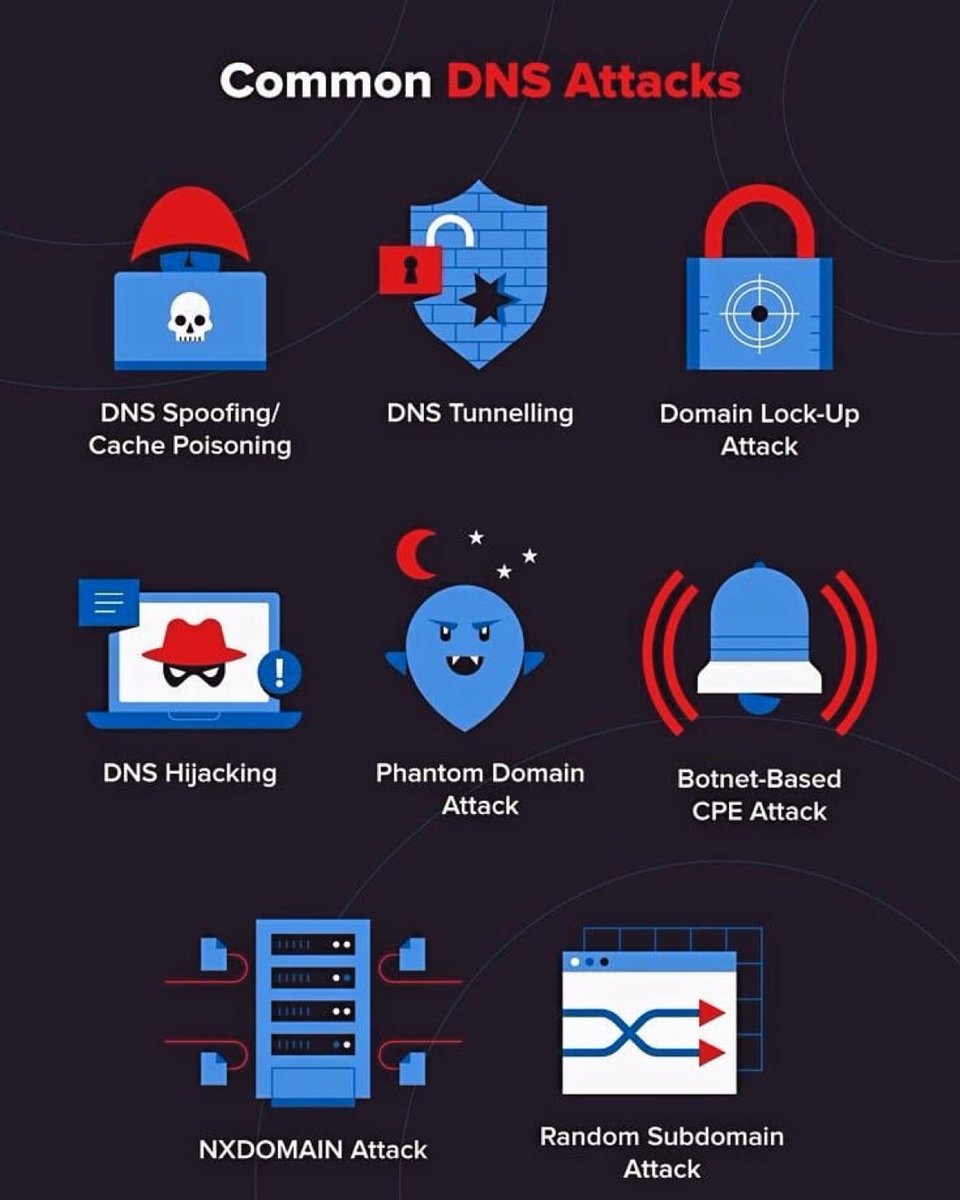
Common #DNS attacks
Follow t.me/Belan_Devx
#Cybersecurity #InfoSec #Ransomware #Phishing #Cybercrime #DataBreach #Hacking #CloudSecurity #NetworkSecurity #IoT #Linux #DataProtection #CyberAttacks #Malware #ThreatIntelligence

A few days ago, Julien Richard, CTO and co-founder at Filigran, was in Washington DC, to meet with our partners in the US Government and provide training for their #OpenCTI developers.
#Partnership #OpenSource #ThreatIntelligence



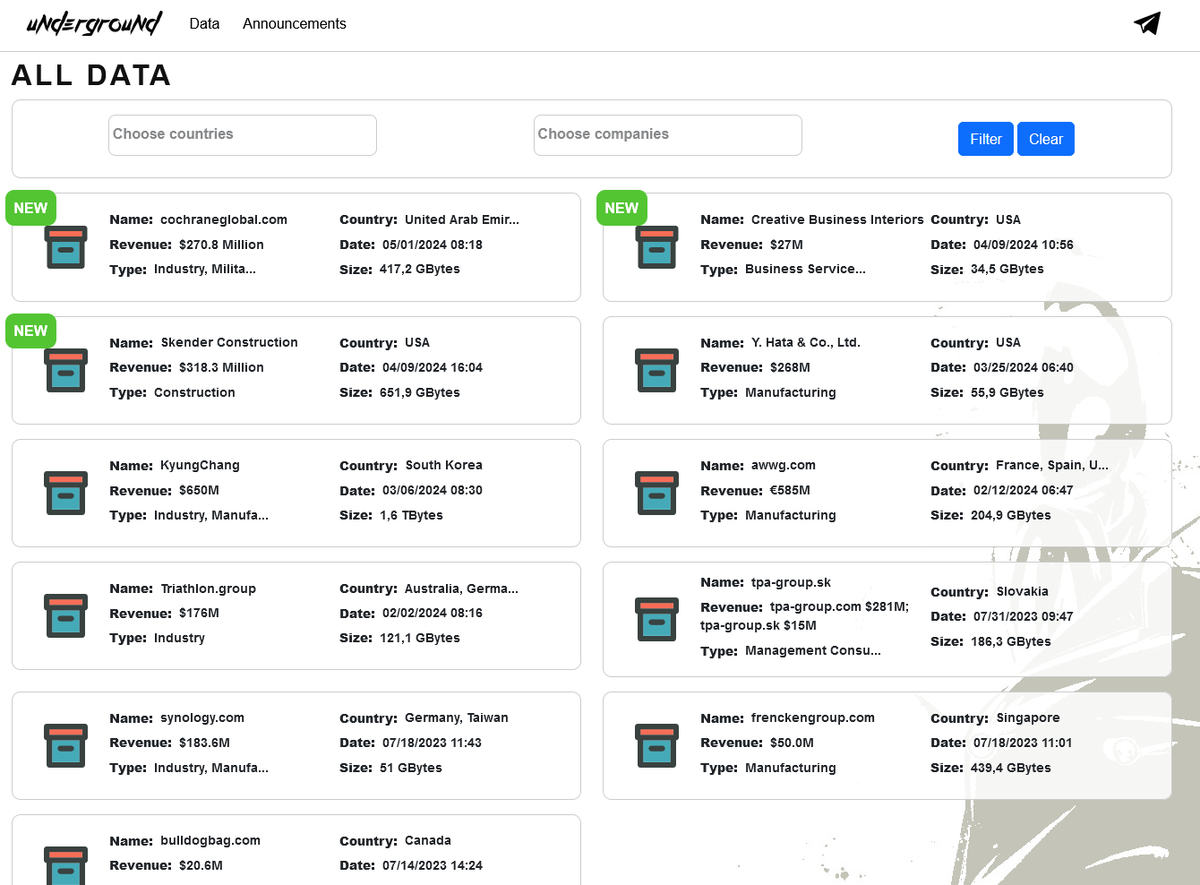
#Underground #Ransomware resurfaced with 11 victims!
…agvrah7gttfscgzn56eyss5wg3uvmqd.onion
Hosted on #nginx
One of the victim is again re-infected by Underground after #Snatch #Ransomware in February!
#infosec #OSINT #darkweb #hack #threatintel #threatintel ligence #security #malware #TOR

Así las cosas:
Jr developer vs state-sponsored actors 😅
#xz #infosec #CyberSecurity #hacking #threatintelligence




Group-IB and NSSG will collaborate on initiatives to raise public awareness about cyber threats and to promote responsible cyber behaviour.
tinyurl.com/29ku6dw3
#corporatenews #fraudprotection #intlbm #partnership #telecom #threatintelligence


Who's watching your network? 🤔 Stay one step ahead of cyber criminals and keep your business safe with these 6 essentials #cybersecurity #continuousmonitoring #threatintelligence #useractivitymonitoring #networktrafficanalysis #SIEM #networksecurity #loganalysis #SIEM