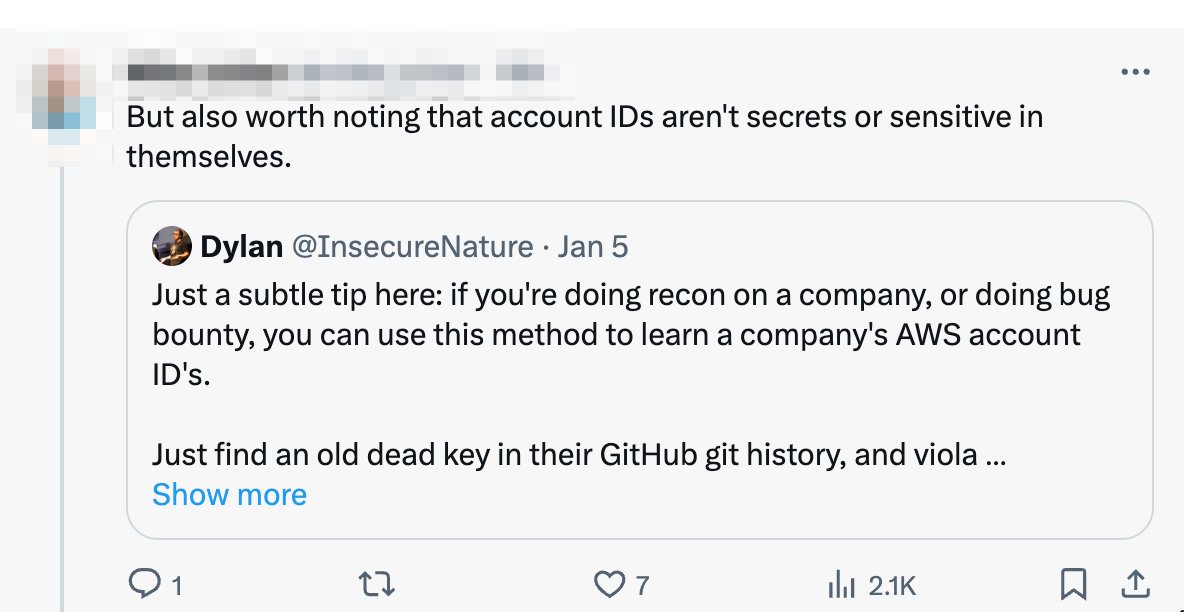
The Sisense breach was rooted in an AWS key in Git.
That got me wondering if #TruffleHog was a musical, what would it sound like...





10th of December: Truffle Security
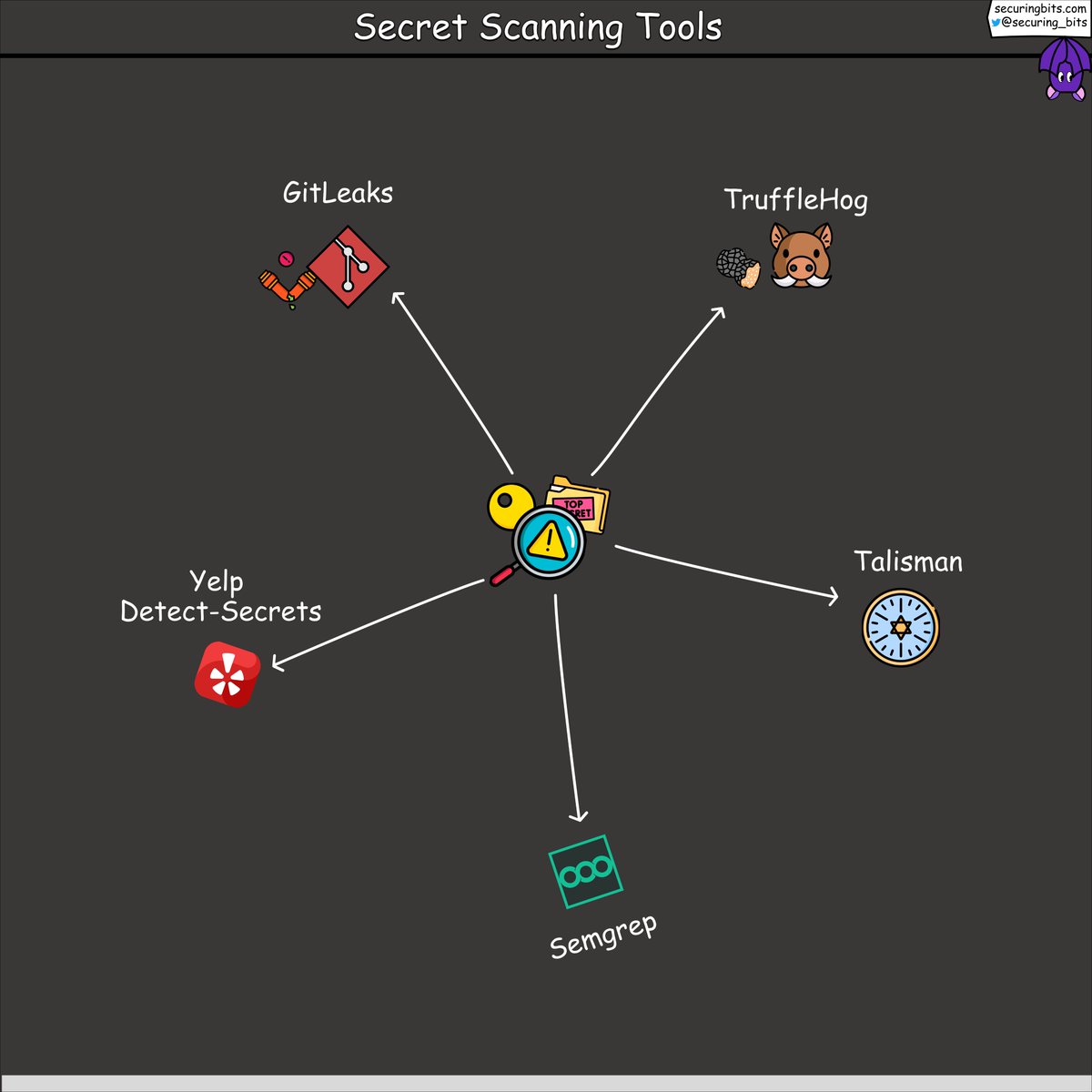
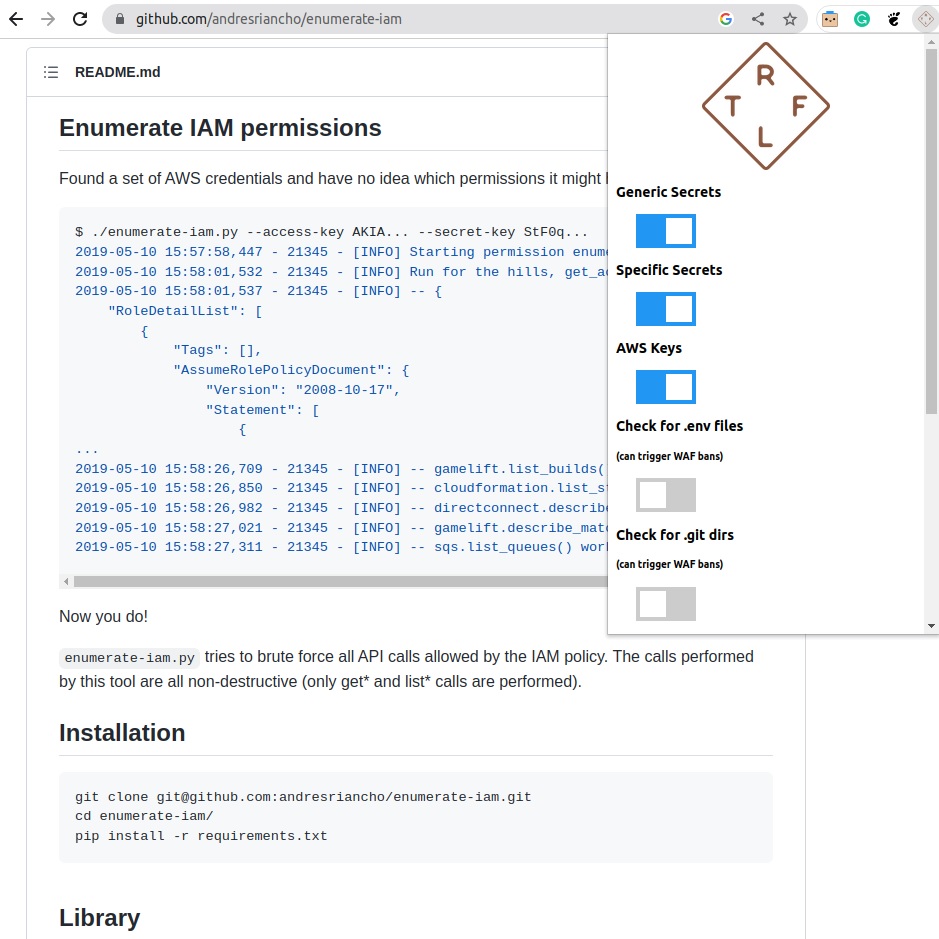
🤔I was researching how to better secure code in my GitHub repos when I met TruffleHog, who checks for hidden secrets !💡
Let me tell you why this secrets-sniffer is so great for keeping my code safe ⤵️



🤔 Why don’t bug bounty programs reward researchers for finding stolen credentials?
🔍We interviewed #HackerOne ’s CISO about new guidelines including:
🔑 Credential types & vulnerabilities
⚖️ Legal risks
🛠️ TruffleHog tools
trufflesecurity.com/blog/bug-bount…

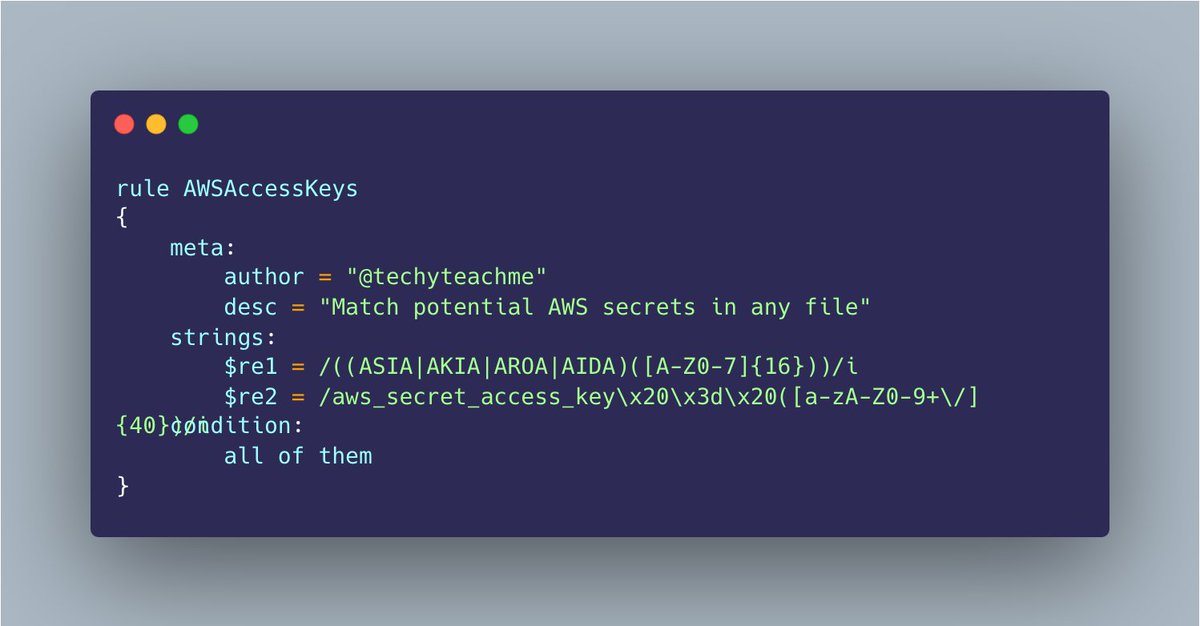
Going through Steve YARA Synapse Miller 's YARA training and playing with atom matching for speed to find aws keys in files #100daysofyara
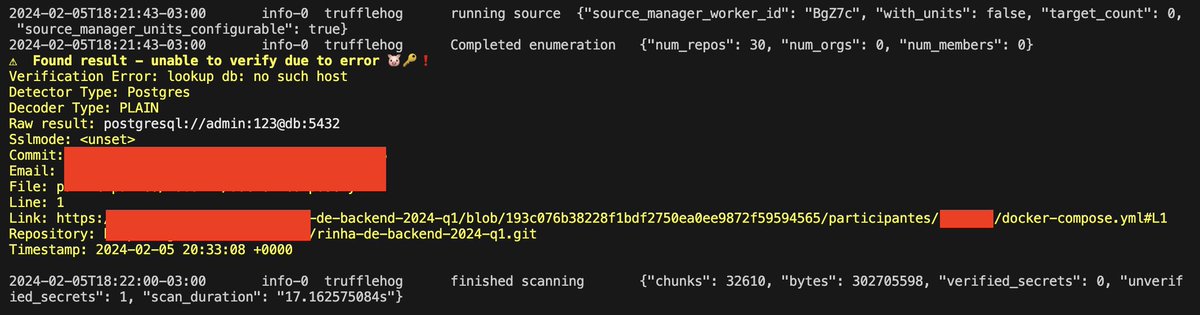
Good and bad guys leave secrets in files. Use regex! Go to Trufflehog, copy regex, load in cyberchef and voila
gist: gist.github.com/zmallen/d2305b…



'So how do you know if you have buried secrets hiding in the vast digital landscape of your organization? Easy. You employ a truffle hog.'
Rooting For Secrets with TruffleHog
by: Chris Traynor
Published: 1/18/2024
Learn more: blackhillsinfosec.com/rooting-for-se…





**NEW** BHIS | Blog
Are your secrets safe?
Rooting For Secrets with TruffleHog
by: Chris Traynor
Published: 1/18/2024
Learn more: blackhillsinfosec.com/rooting-for-se…



'Identifying and cleaning up leaked secrets before an attacker can find them is a crucial component to security.'
Rooting For Secrets with TruffleHog
by: Chris Traynor
Published: 1/18/2024
Learn more: blackhillsinfosec.com/rooting-for-se…