
Is mandatory password expiration helping or hurting your password security?
#DataSecurity #Privacy
#100DaysOfCode #CloudSecurity
#MachineLearning #Phishing #Ransomware #Cybersecurity #CyberAttack #DataProtection
#DataBreach #Hacked #Infosec


Wondering how to #Recover , #hacked , retrieve, or protect any accounts or wallets DM now
#CyberSecurity #hacker #infosec Techryptic, Ph.D. #opensource #crime #gdpr #cloud #cloud security #dataprotection #Privacy #cloud computing #malware #ransomware #100DaysOfHacking #100DaysOfCode


For support and help, contact your favorite Hacker @James_cyber01 for All social media Accounts recovery &Spy #CyberSecurity #hacker #infosec #Snapchat #security #cyber #opensource #crime #gdpr #cloud #cloud security #dataprotection #Privacy #Instagram #Tiktok #malware #ransomware


Wondering how to #Recover , #hacked , retrieve, or protect any accounts or wallets DM now
#CyberSecurity #hacker #infosec Techryptic, Ph.D. #opensource #crime #gdpr #cloud #cloud security #dataprotection #Privacy #cloud computing #malware #ransomware #100DaysOfHacking #100DaysOfCode
I

8 strange ways emproyees can (accidently) expose data
bit.ly/3M633Dj
#DataSecurity #Privacy
#100DaysOfCode #CloudSecurity
#MachineLearning #Phishing
#Ransomware #Cybersecurity #CyberAttack #DataProtection
#DataBreach #Hacked #Infosec


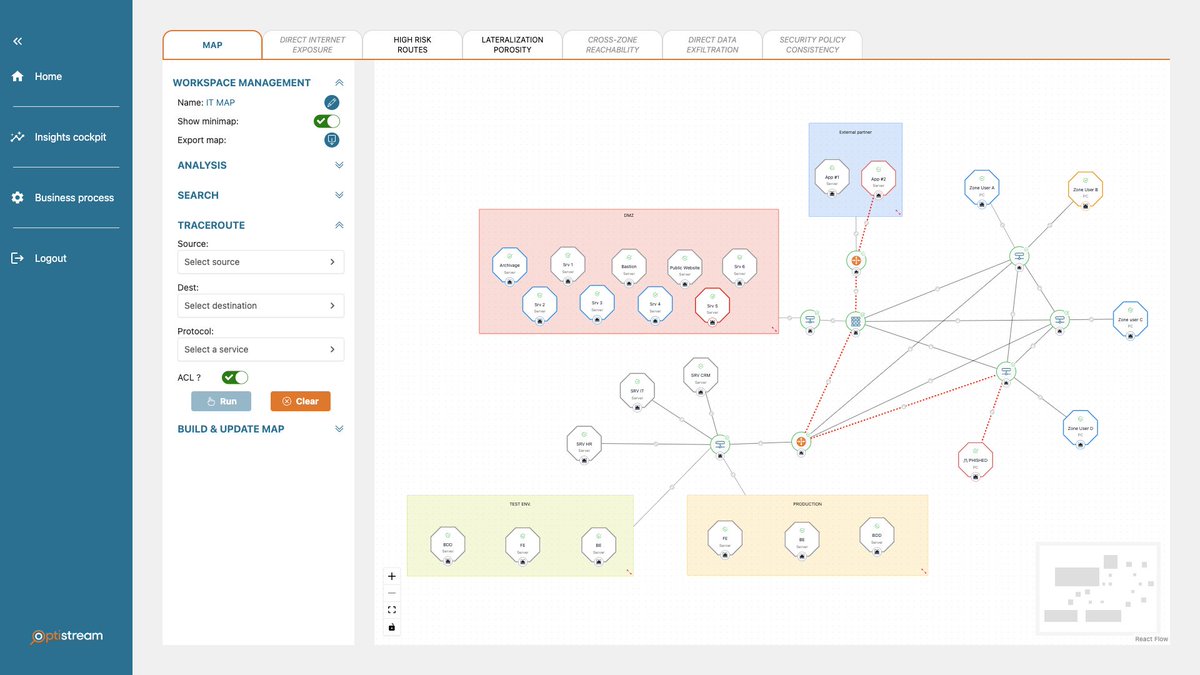
Big news today!
We are thrilled to launch Optistream NetTwin!
Result of months of R&D, this groundbreaking solution offers intelligent network maps to secure hybrid infrastructure (inc. AWS). (1/3)
#cybersecurity #network #OT #cloudsecurity

Did you lose your account and you want it back but don't know how❓
Let me help🤗
#facebookads #facebookdown #Facebook #Facebook Live #facebookhacked #100DaysOfCode #CloudSecurity
#MachineLearning #Phishing #Ransomware #Cybersecurity #CyberAttack #facebook_twitter #facebookdown i


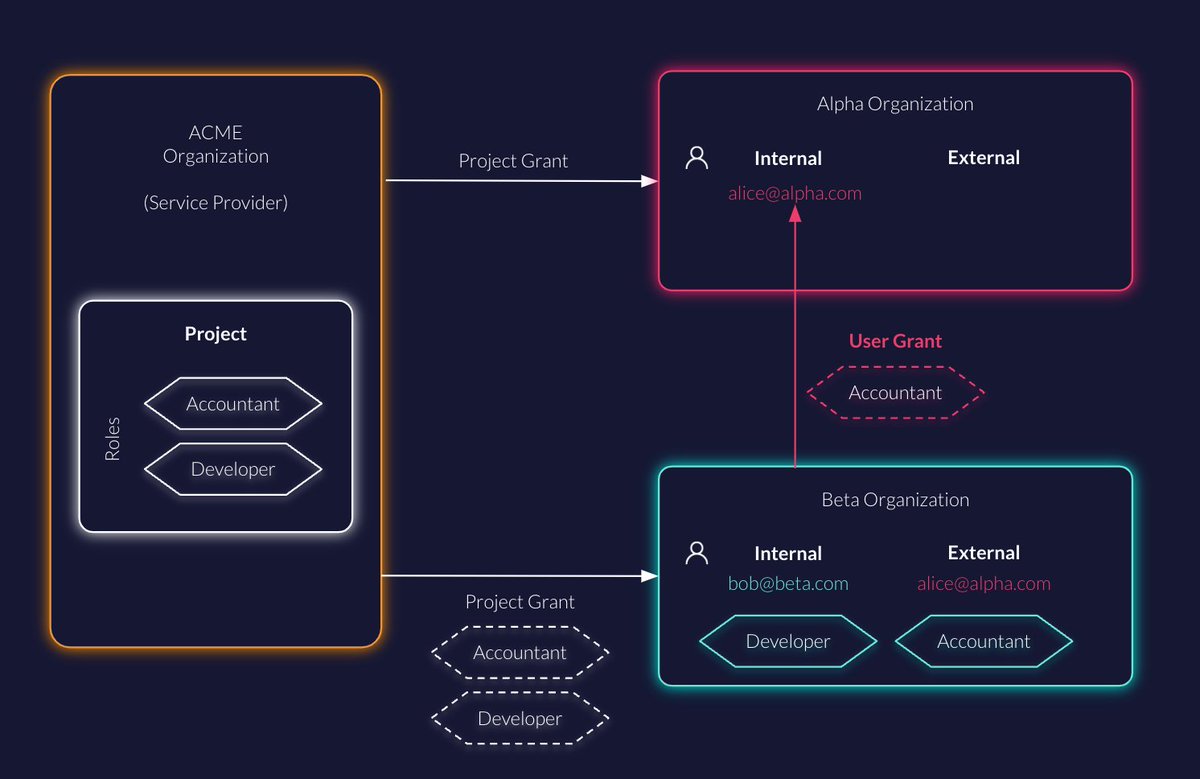
Simplify B2B collaboration! Grant access to specific users from other orgs in #zitadel with external user grants: zitadel.com/docs/concepts/… #cloudsecurity #multitenancy

☁️ Advanced cloud services protect every transaction with SecurCom. Welcome to the next level of financial service security.
#CloudSecurity #SecurCom #SecurePayments 🛡️



Join professionals from industries like #government , #security and dive into the #cybersecurity and #cloud ecosystem at the Cyber Security & Cloud Expo this June 5-6. Topics include tenants of CISO success, #cloud security, and more.
Register here: bit.ly/3RSjlmf#CyberE…



btw I am on the lookout for security engineer/cloud security roles. If you are someone who is #hiring , here is your chance to #hire me😅.
About me and my blog website: noshellaccess.com/aboutme/
My portfolio: pankajmouriya.com
#securityengineer #cloudsecurity

Hi Cloudsec community ! I would like to share with you a first iteration of a list of awesome cloud security events/conferences over the year. Feel free to make suggestions!
github.com/qbrusa/Awesome…
#Cloud #cloudsecurity fwd:cloudsec Cloud IdentitySummit SecurityWeek SANS Cloud Security

For support and help, contact your favorite Hacker @James_cyber01 for All social media Accounts recovery &Spy #CyberSecurity #hacker #infosec #Snapchat #security #cyber #opensource #crime #gdpr #cloud #cloud security #dataprotection #Privacy #Instagram #Tiktok #malware #ransomware


Cloud security is 🔑! Don't let hackers make your cloud their playground. 🚫 Stay ahead of cyber threats with multi-factor authentication and robust identity protection. Read more: buff.ly/4d5CUSj 🛡️ #cloudsecurity #cybersecurity


Big news in #CyberSecurity : Wiz has acquired Gem Security, a game-changing move to enhance #CloudSecurity solutions. Excited for the innovative future this collaboration promises. Congrats to Wiz and Gem Security
#TechAcquisition #Partnerships

For threat detection in cloud, the logic to identify a threat can be trivial, but discerning between benign and malicious is often the hardest challenge, especially for traditional detection engines that rely on statically defined rules. #threatdetection #cloudsecurity

