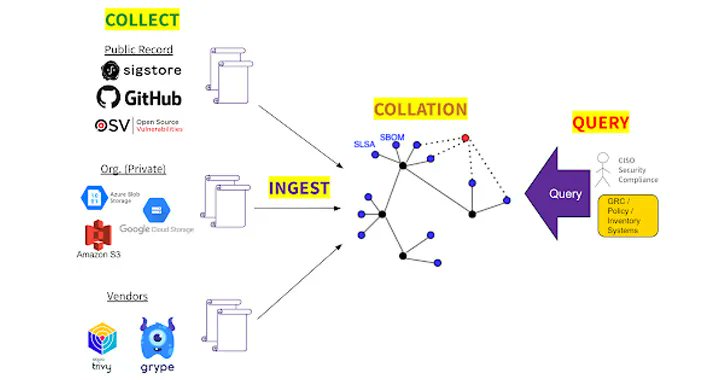
Toyota Motor Corporation has discovered two additional misconfigured cloud services that leaked car owners' personal information for over seven years. buff.ly/43Bm48a Riskigy #cybersecurity #riskigy #security #psa #knowledgeshare #cyberawareness #riskalert #vciso



A new security flaw has been disclosed in the #Google Cloud Platform's (GCP) Cloud SQL service that could be potentially exploited to obtain access to confidential data. buff.ly/3MZH6Ii Riskigy #cybersecurity #riskigy #security #knowledgeshare #cyberawareness #vciso



Swiss tech multinational and U.S. government contractor ABB has confirmed that some of its systems were impacted by a ransomware attack, previously described by the company as 'an IT security incident.' buff.ly/43nPEOo Riskigy #cybersecurity #riskigy #knowledgeshare


Enterprise security firm #Barracuda on Tuesday disclosed that a recently patched zero-day flaw in its Email Security Gateway (ESG) appliances had been abused by threat actors since October 2022 to backdoor the devices. buff.ly/3C3k9O5 Riskigy #cybersecurity #riskigy





Kali Linux 2023.2, the second version of 2023, is now available with a pre-built Hyper-V image and thirteen new tools, including the Evilginx framework for stealing credentials and session cookies. buff.ly/3IMBdLW Riskigy #cybersecurity #riskigy #security #cyberawareness




An updated version of the commodity malware called Legion comes with expanded features to compromise SSH servers and Amazon Web Services #AWS credentials associated with DynamoDB and CloudWatch. buff.ly/3BUAgxk Riskigy #cybersecurity #riskigy #security #cyberawareness



Improperly deactivated and abandoned Salesforce Sites and Communities (aka Experience Cloud) could pose severe risks to organizations, leading to unauthorized access to sensitive data. buff.ly/45BpycP Riskigy #cybersecurity #riskigy #security #knowledgeshare #riskalert


Apple has recently addressed a vulnerability that lets attackers with root privileges bypass System Integrity Protection (SIP) to install 'undeletable' malware. buff.ly/3oD1WUA@riskigy #cybersecurity #riskigy #security #knowledgeshare #cyberawareness #riskalert #vciso


Hackers hold city of Augusta hostage in a #ransomware attack and released 10GB of sample data from the #cyberattack on the US city of Augusta and claimed they have a lot more data available. buff.ly/3N3vtjA Riskigy #cybersecurity #riskigy #security #psa #knowledgeshare