'Secure and Smart Internet of Things ( #IoT ): Using #Blockchain and Artificial Intelligence ( #AI )'
amzn.to/3gT2Kye
————
#BigData #IIoT #DataScience #MachineLearning #IoT Security #DataSecurity #Infosec #CyberSecurity #Edge #Edge Computing


Increased device connectivity means increased #cyberthreats . Learn how @CiscoIoT Cyber Vision provides unprecedented scale & simplicity to your #IoT security needs: oal.lu/fBgya #cybersecurity #IoT


Peering into the Future: The Next Wave of IoT Security Technologies 🌐🔐.
Let's dive into the future of IoT security together.
#EmergingTech #IoTSecurity #FutureReady #SmartInnovation


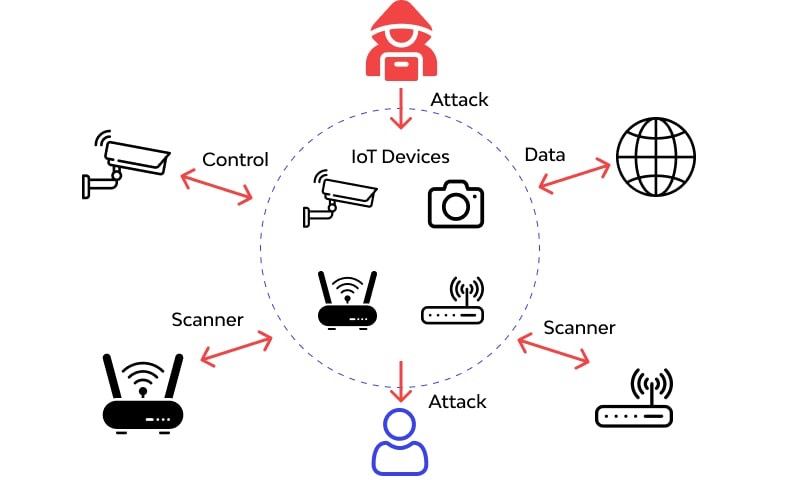
🚨 Stay vigilant against IoT attacks! These cyberattacks target IoT devices, allowing hackers to take control, steal data, or form botnets for launching DoS/DDoS attacks. #IoTsecurity #CyberSecurity #Botnet #DDoSProtection 🛡️

Update to Elevate: Your IoT Security's First Shield! 🔒💻 Ever hit 'remind me later' on a software update?
Let's make a pact to prioritize updates, keeping our smart devices not just smarter, but safer.
#UpdateYourDefense #IoTSecurity #CyberSafety #KlosConsulting


[Case study] A Global Manufacturer’s Journey to Automating PKI with Keyfactor
buff.ly/4aRoCCX
#sponsored #keyfactor_ics #IoTsecurity #cybercommunity Michael E Lemm Bob Carver ✭ via IIoT World
![IIoT World (@IIoT_World) on Twitter photo 2024-04-22 19:00:20 [Case study] A Global Manufacturer’s Journey to Automating PKI with Keyfactor
buff.ly/4aRoCCX
#sponsored #keyfactor_ics #IoTsecurity #cybercommunity @FreedomFireCom @cybersecboardrm via @IIoT_World [Case study] A Global Manufacturer’s Journey to Automating PKI with Keyfactor
buff.ly/4aRoCCX
#sponsored #keyfactor_ics #IoTsecurity #cybercommunity @FreedomFireCom @cybersecboardrm via @IIoT_World](https://pbs.twimg.com/media/GLyoS8TW0AAxd01.jpg)


Motivations and challenges of industrial digital transformation buff.ly/3vk2QbM
#sponsored #keyfactor_ics #iotsecurity #digitaltransformation Michael E Lemm via IIoT World


The role of digital trust in an untrusting world buff.ly/3VWd5y6
#sponsored #keyfactor_ics #DigitalTrust #IoTsecurity #cybercommunity #cybersecurity 🟣Tyler Cohen Wood Ratan Jyoti via IIoT World


CISA opens its malware analysis and threat hunting tool for public use
csoonline.com/article/208951… #IoTMalware #IoTSecurity #IoTDevelopment

Announcing @guidepointsec's latest offering: #IoT Security Assessments. Gain comprehensive insights into IoT devices, covering components, firmware, networking and management systems. Learn more. okt.to/Bkcowi #cybersecurity #IoT Security



Digital Trust in Manufacturing: A Cornerstone for Security, Innovation, and Growth buff.ly/3VWd5y6 #sponsored #keyfactor_ics #Manufacturing #IoTsecurity #industry40 Dr. Hassan Rashidi Andrei Fogoroș via Lucian Fogoros


Unlock Strength with Smart Passwords for Your Smart Devices 🔐✨.
As our homes and lives become more connected, enhancing IoT security with strong authentication becomes crucial.
#SmartPasswords #IoTSecurity #DigitalFortress #StrongAuthentication #KlosConsulting


Key takeaways from Forrester’s Top Trends in IoT Security 2024 #SecurityByDesign #IoT #IoT Security #AI #AI oT Forrester VentureBeat LouisColumbus venturebeat.com/security/key-t…


Explore hardware hacking in the latest blog from Nathan Keys [Nathan Keys], Security Consultant, Threat and Attack Simulation. Learn the essentials of IoT device assessment, from functional evaluation to firmware analysis. okt.to/jhwBtP #IoTSecurity #Cybersecurity
![@guidepointsec (@GuidePointSec) on Twitter photo 2024-04-16 17:43:03 Explore hardware hacking in the latest blog from Nathan Keys [@_v3rtigo_], Security Consultant, Threat and Attack Simulation. Learn the essentials of IoT device assessment, from functional evaluation to firmware analysis. okt.to/jhwBtP #IoTSecurity #Cybersecurity Explore hardware hacking in the latest blog from Nathan Keys [@_v3rtigo_], Security Consultant, Threat and Attack Simulation. Learn the essentials of IoT device assessment, from functional evaluation to firmware analysis. okt.to/jhwBtP #IoTSecurity #Cybersecurity](https://pbs.twimg.com/media/GLTdEaQXQAAX3dO.jpg)

Announcing @guidepointsec's latest offering: #IoT Security Assessments. Gain comprehensive insights into IoT devices, covering components, firmware, networking and management systems. Learn more. okt.to/gaeRUV #cybersecurity #IoT Security


The Internet of Things (IoT) has introduced a new frontier of cyber security challenges. With more devices connected than ever before, it's crucial to secure each endpoint to prevent potential breaches. #IoTSecurity #ConnectedDevices