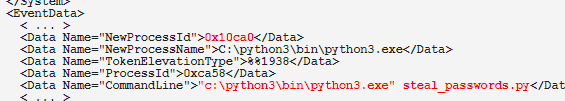


As a DFIR Engineer, you should notice something suspicious going on here!!
But how many techniques do you know that an attacker can use to hide this easy detection from you?!
#C5W #DFIR #Malware #ThreatHunting #Cybersecurity










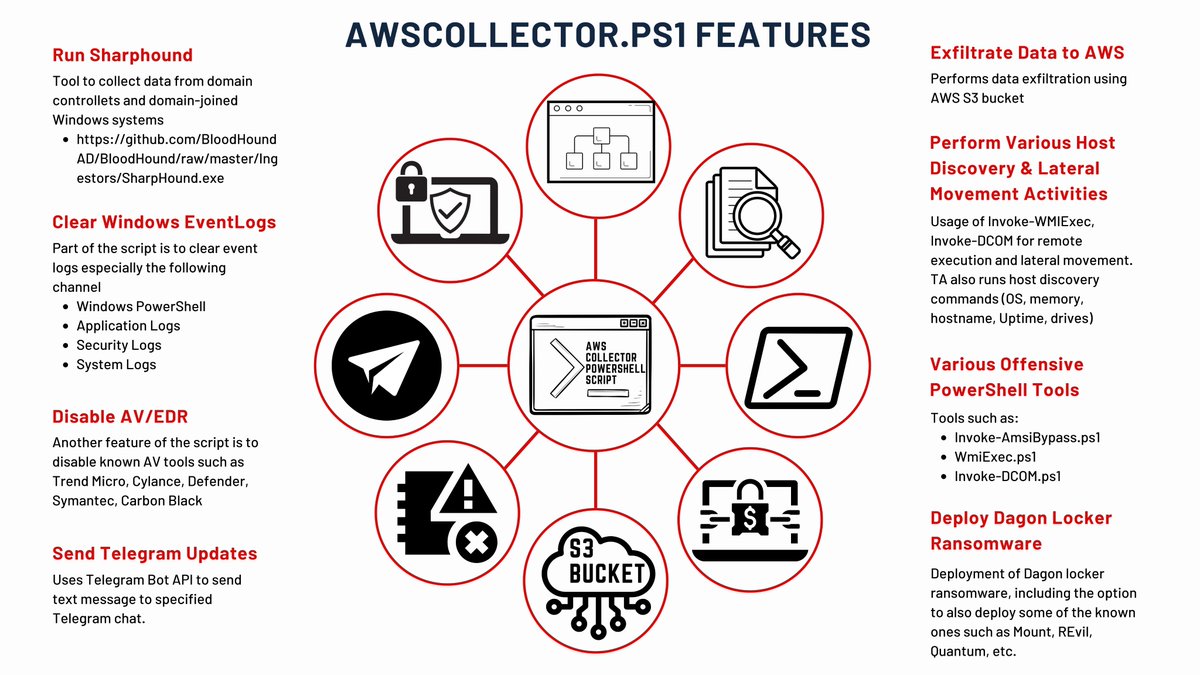
I had the opportunity to co-author this blog. This case started from IcedID to Cobalt Strike to deploying Dagon Locker RW. This case had a TTR (time to ransomware) of 29 days. It's a long report with lots of graphics. Hope you like it The DFIR Report #DFIR
thedfirreport.com/2024/04/29/fro…