#1 thing when building a career
#BeABetterArtist #MusicPodcast #creativecareer #creativity #musician #career #reverseengineering

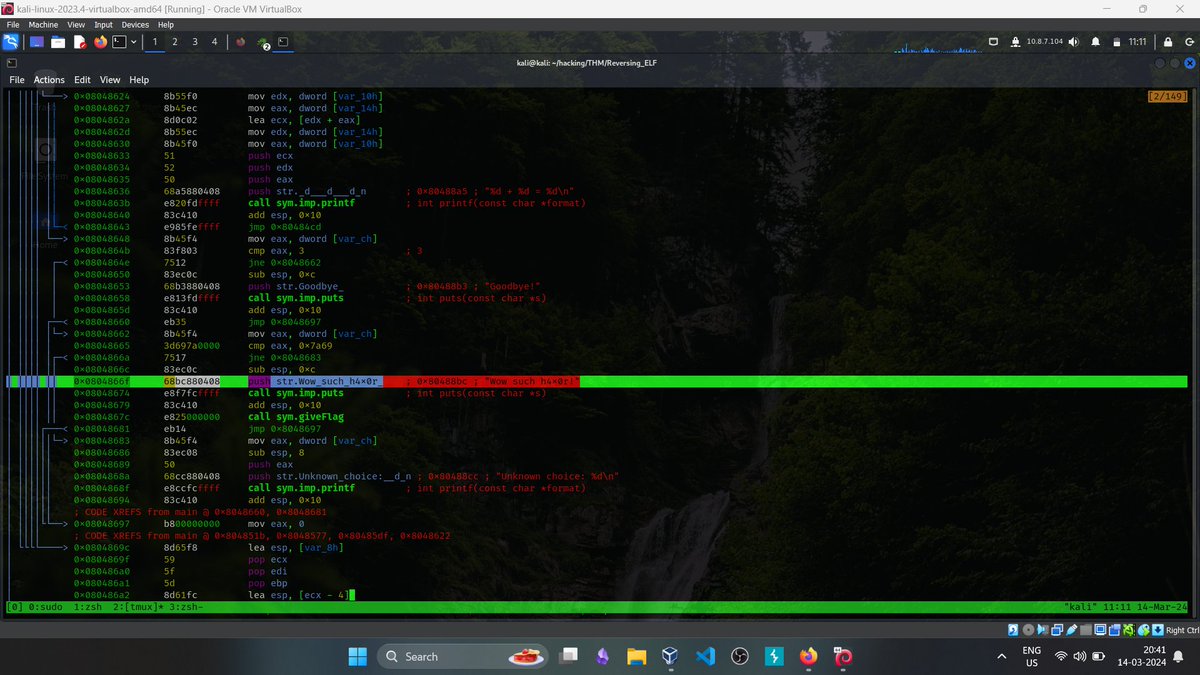
CTF No: 27/100
Platform: TryHackMe
Name: Reversing ELF
Difficulty: Easy
Skills: Reverse Engineering, ELF file analysis, Radare2 (R2), x86 Assembly, Binary Exploitation
#ctf #Cybersecurity #Hacking #ReverseEngineering #TryHackMe #THM

Some friends of mine gave me some Kraze HD7K disposable vapes that have color LCD screens(!), and I've been spending the past days #reverseengineering them.
Shenanigans have already ensued. I edited the onboard SPI Flash with new images :3
Research log: github.com/ginbot86/Color…

#reverseengineering 'The Picture of Dorian Grey'. Saw a sampling (?) project by @tim_rodenbroeker (🔗 below) and plunged down a fun rabbit hole. 💻 openprocessing.org/sketch/2264236 🎵pixabay.com/music/nostalgi… #p5js #creativecodeart #creativecoding #proceduralart #mathart #codeart

Hey everyone 🫡
I have written my first blog on x86 ASM.
This is related to step by step understanding of x86 via GetVersion() API call walkthrough.
Do checkout 👇
blog.fautl.com/x86-via-GetVer…
#cybersecurity #ReverseEngineering #exploitation #AssemblyLanguage #MalwareAnalysis




Early experiments in bezier curves from a couple of years back. Can’t remember where I saw something similar but thought I’d give it a crack. I see Kiwis? #WIP #creativecoding #genart #generativeart #bezier #mathart #p5js #processing #reverseengineering #RecodeRethink

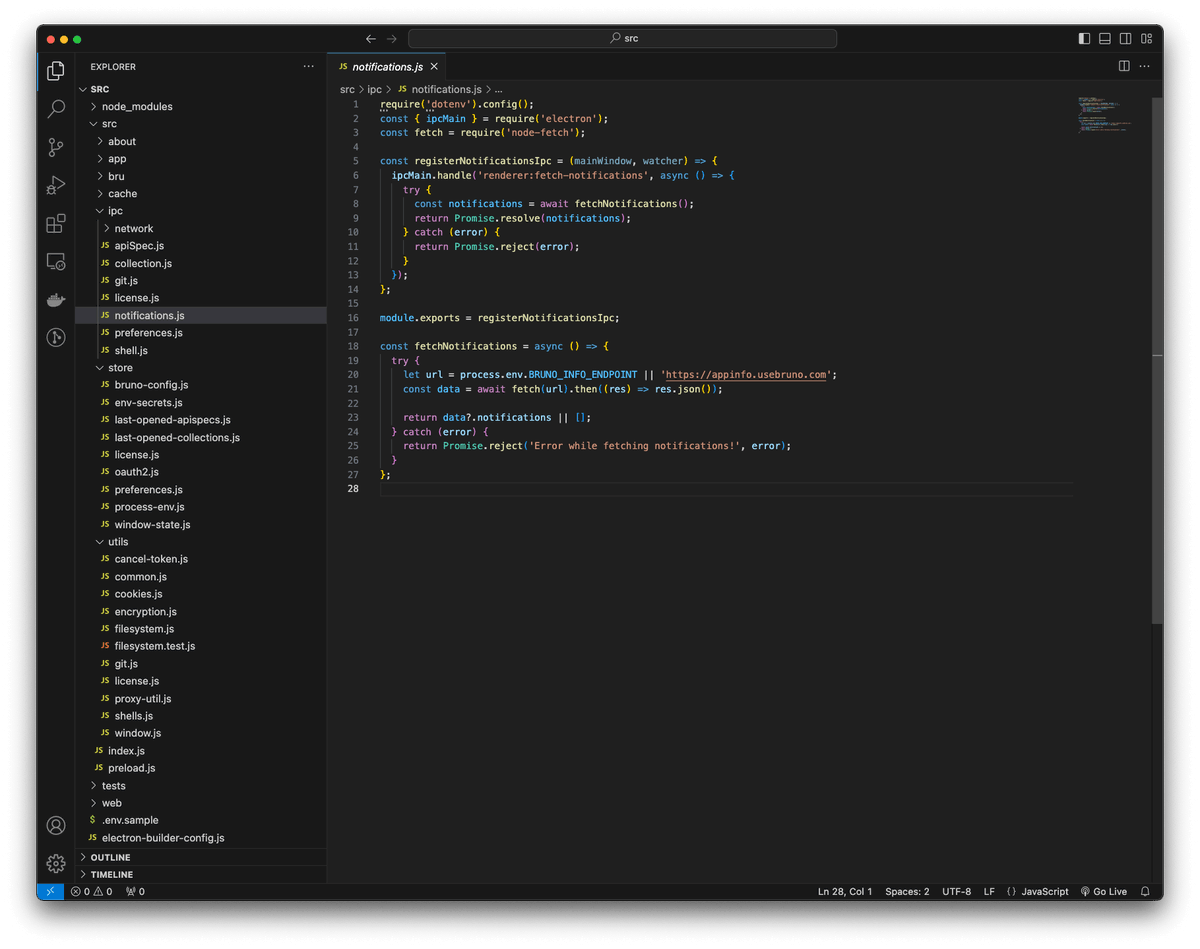
Reverse Engineering Electron Apps to Discover APIs danaepp.com/reverse-engine… #Pentesting #ReverseEngineering #CyberSecurity #Infosec

50+ years of experience, a 10,000 sq metre foundry and complete on-site production - what more could you need for your casting requirements?! 🔥
Hit play to see more on what we do at our foundry. ▶️
#Casting #MetalCasting #MetalFoundry #Manufacturing #ReverseEngineering #CNC

I’ve been #reverseengineering #Gremlins for the #atari2600 out of curiosity. There is no official PAL50 release of this but there will be a proper PAL50 and PAL60 when I’m done.


Chapter 34: Hacking Dynamic Conditionals 📷 Hack at the Assembler level and learn to understand how dynamic conditionals work in memory as we reverse engineer an embedded binary! #CyberSecurity #Embedded #Development #ReverseEngineering github.com/mytechnotalent…


🚀🚀🚀 New Blog Alert! In Part 2 of our Dissecting Windows Malware Series, we dive deeper into how Process Injections work on the Windows platform.
Read Here 👉 8ksec.io/dissecting-win…
#MalwareAnalysis #Windows #ReverseEngineering


🚀🚀🚀 New Blog Alert! Learn the foundations of analyzing and reverse engineering Windows Malware in Part 1 of our Series on Dissecting Windows Malware - 8ksec.io/dissecting-win…
#Windows #malware #MalwareAlert #reverseengineering


Explore Geomagic 3D Design software, developed by Oqton for precision and efficiency.
Ideal for engineering, manufacturing and design, it enhances workflows and brings visions to life.
Learn more: central-scanning.co.uk/product-catego…
#Geomagic #3DSoftware #Oqton #reverseengineering

Last day to submit your CFP for Recon recon.cx #reverseengineering #infosec #cybersecurity

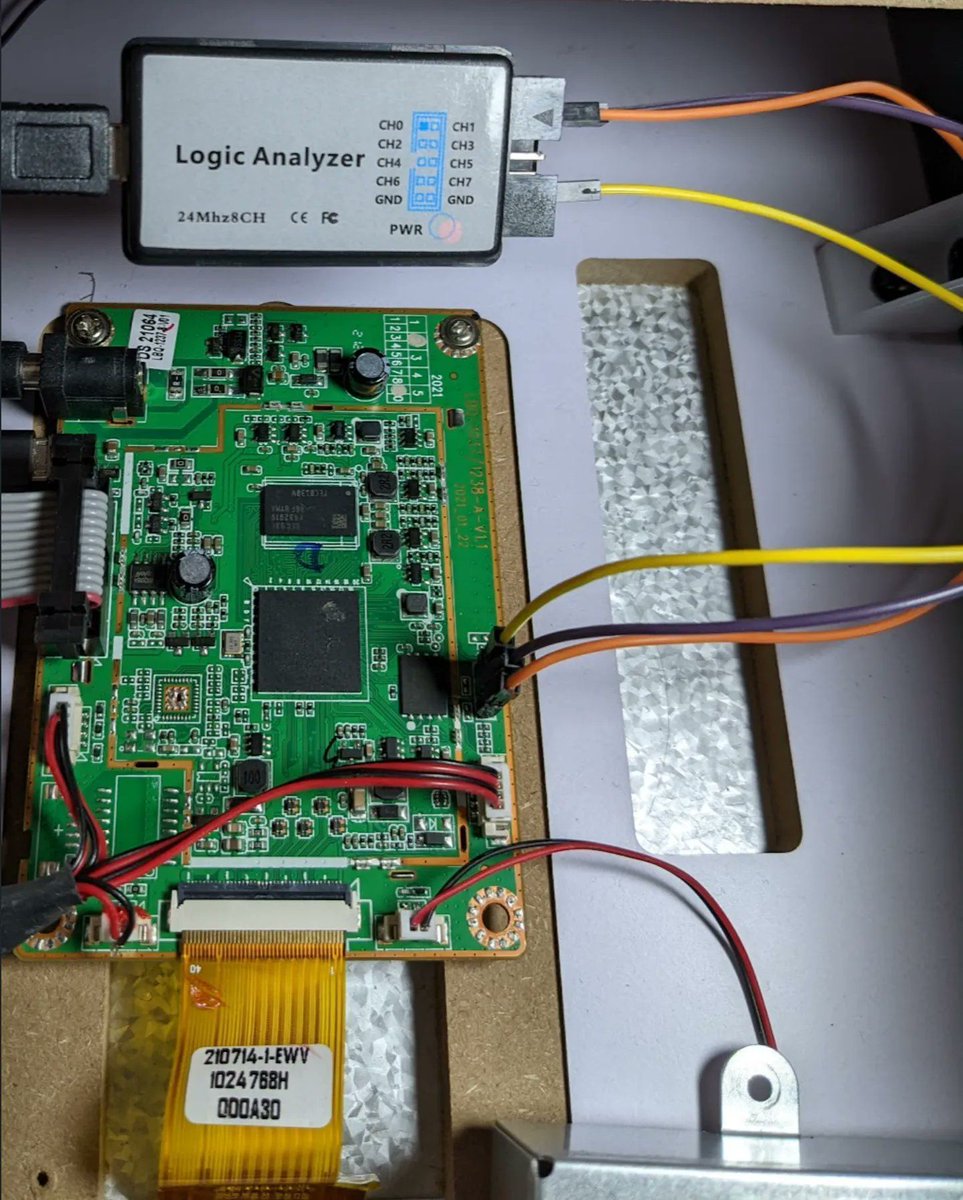
Starting with embedded devices reverse engineering (Beginners series)
Credits VoidStar Security LLC
Ghidra setup: voidstarsec.com/blog/ghidra-de…
Tools: voidstarsec.com/blog/intro-to-…
Firmware extraction: voidstarsec.com/blog/uart-uboo…
#reverseengineering #cybersecurity

🚀New Blog Alert! 🚀🚀 Learn how Windows malware use data encoding to their advantage in Part 3 of our Dissecting Windows Malware Series Read Here 👉 8ksec.io/dissecting-win….
Follow us 8kSec for more such content.
#MalwareAnalysis #Windows #ReverseEngineering #DFIR


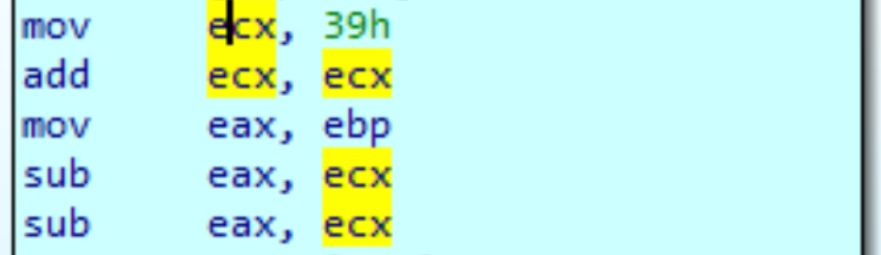
RE tip of the day: To obfuscate malware, attackers may introduce garbage instructions that don't do anything useful related to the actual logic or expand existing ones by replacing them with multiple others doing the same thing
#infosec #cybersecurity #malware #reverseengineering