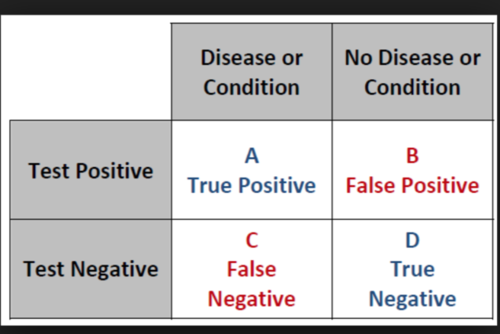
#12 #truenegative #dailycue
Eg: Model predicting person X is negative to a disease and the person actually is
#ai #ml #datascience #basics_of_ai #dailypost #learning #bysri



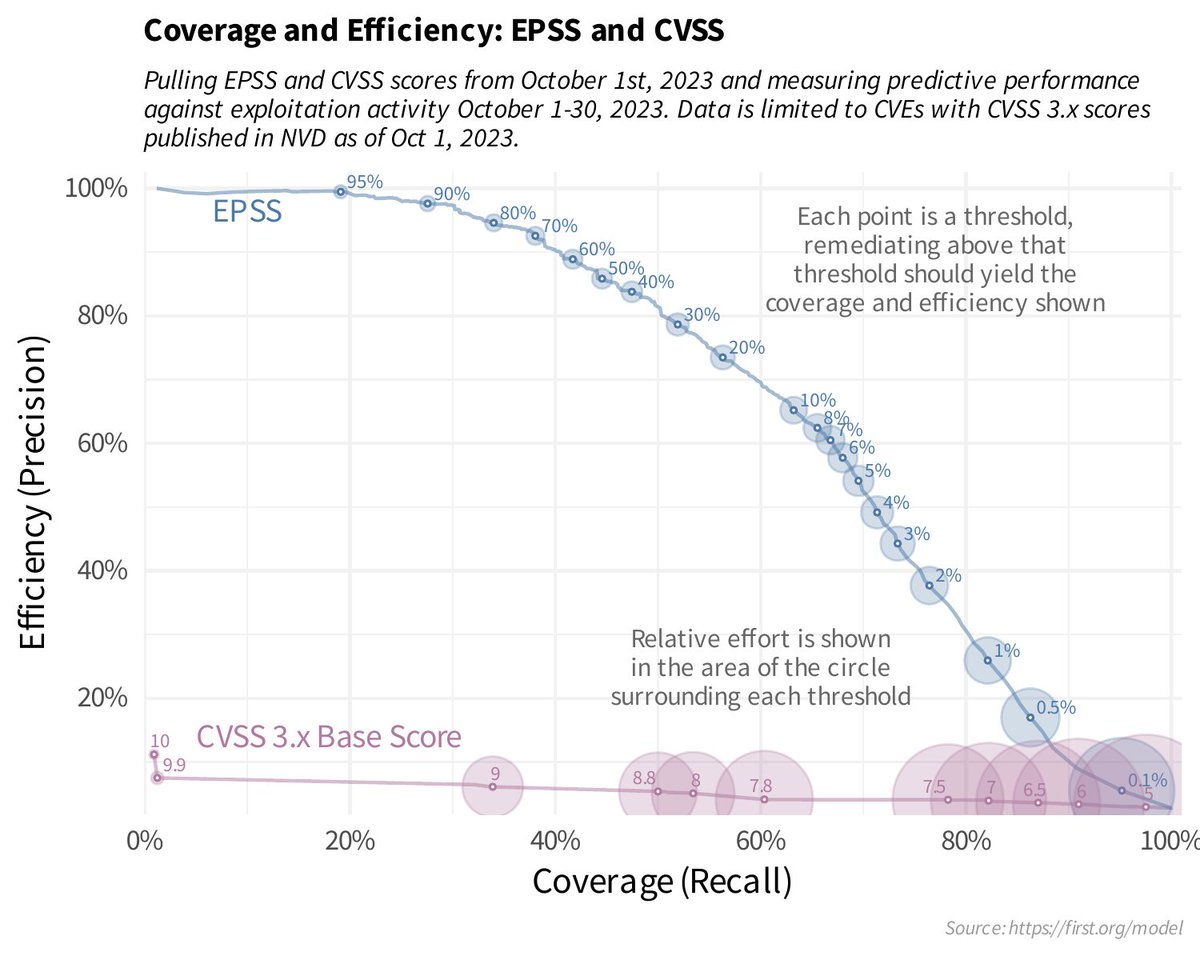
#VulnerabilityManagement : #EPSS and #CVSS vs #risktolerance and #budget
#TrustEverybodyCutCutTheCards
We can these #truepositive , #falsepositive , #falsenegative and #truenegative vulnerability categories to derive three more meaningful metrics:


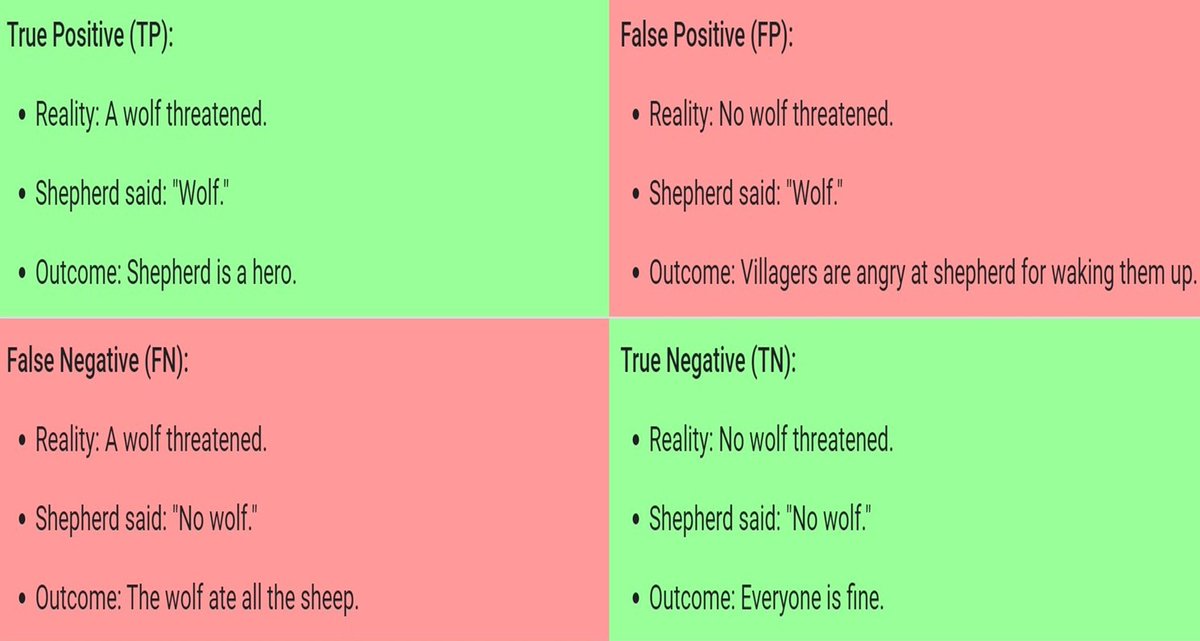
Know and don't get confused. Thanks, Google guys. True Positive (TP) False Positive (FP) False Negative (FN) True Negative (TN) #TruePositive #FalsePositive #FalseNegative #TrueNegative #machinelearning #datascience #classification #prediction #modeling #accuracy #precision

🧑🏽💻 #ConfusionMatrix #Cheat Sheet ✍🏽 - Read 👇🏽👇🏽👇🏽
📪 In the post, let's discuss
1️⃣ #PositivePredictiveValue
2️⃣ #Sensitivity or True Positive Rate
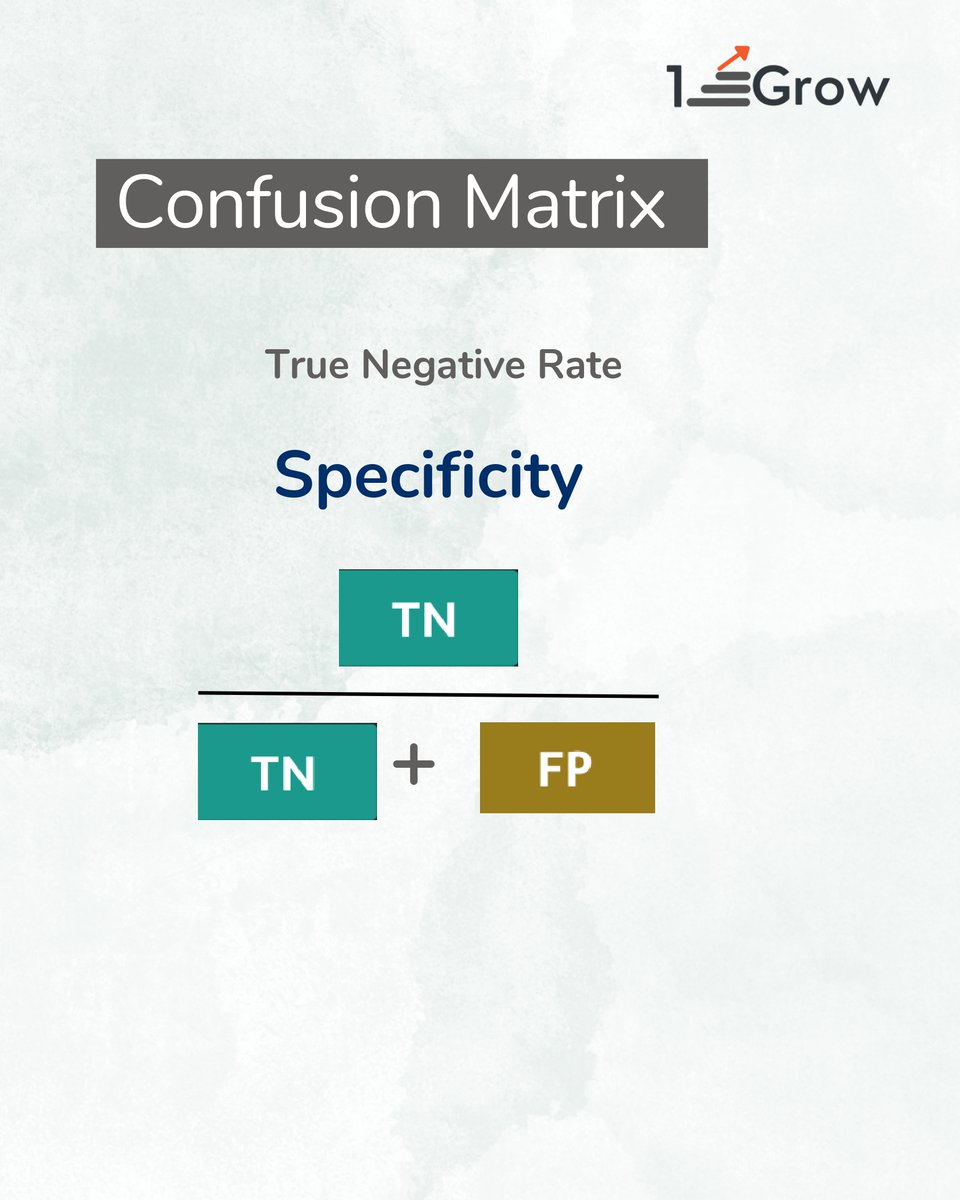
3️⃣ #TrueNegative Rate
4️⃣ #NegativePredictiveValue
🎈 Follow 1stepGrow to get informative and learning posts.



750$ for Stealing Facebook OAuth Code Through Screenshot viewer
Taking advantage of an image injection vulnerability in the Screenshot Viewer utility as well as additional vulnerabilities still being resolved.
hackerone.com/reports/488269 #bugbounty
#cybersecurity #infosec

Hack The Box - Insane Ethereal write-up by 0xRick
0xrick.github.io/hack-the-box/e…
#hackthebox #infosec #cybersecurity

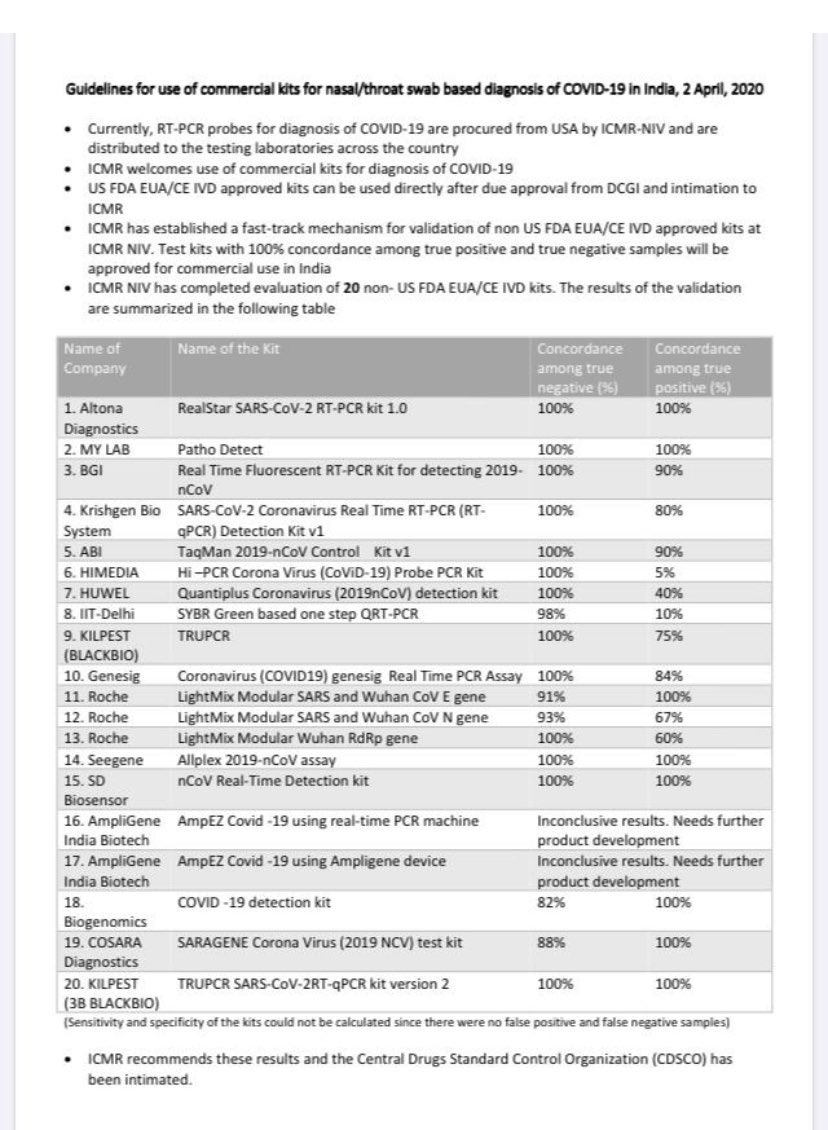
#COVIDpandemic #CoronaInMaharashtra #COVID2019 #India private labs, testing kits and concordance #TrueNegative #TruePositive
World Health Organization (WHO) Anant Bhan






1000$ for Access to Employee calendar disclosing internal presentation and meetings.
hackerone.com/reports/489284 #bugbounty #infosec #cybersecurity


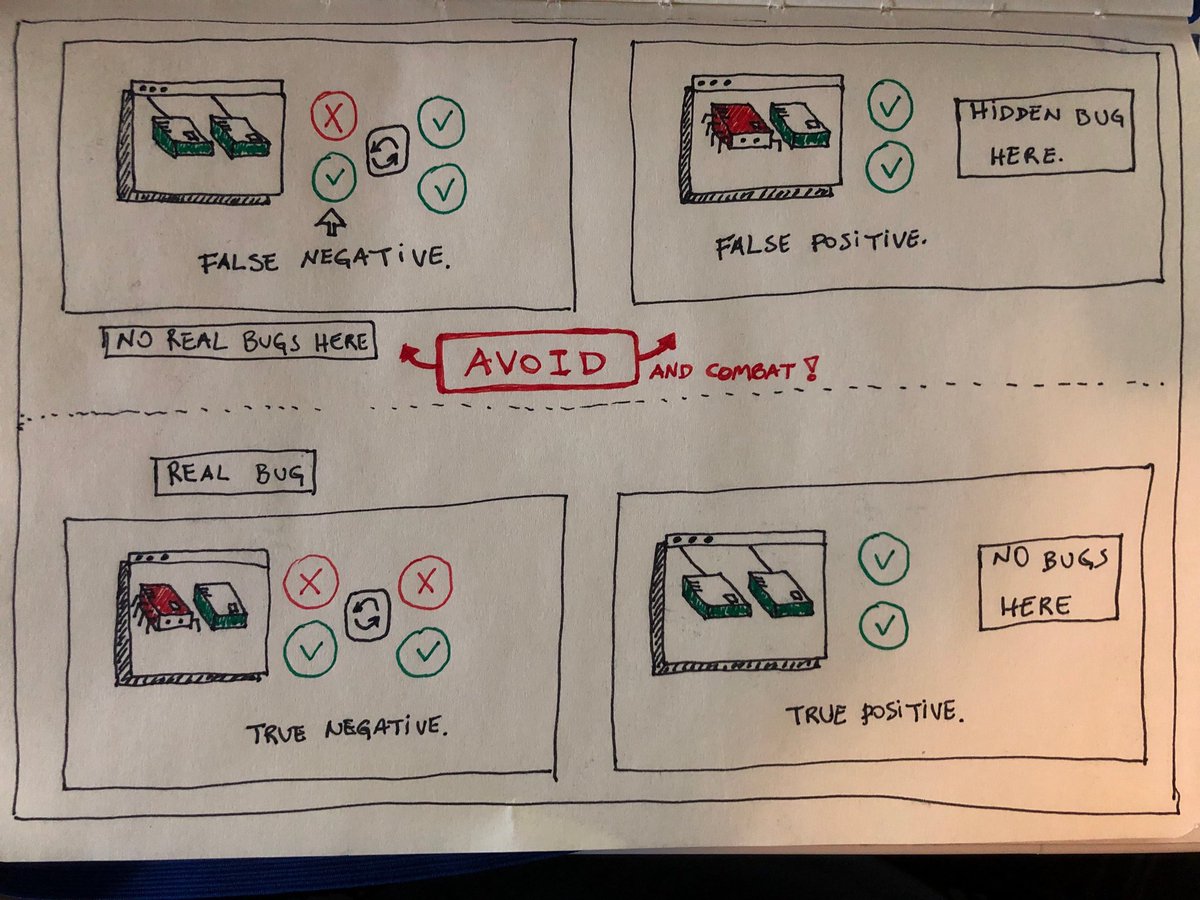
#falsepositive , #truepositive , #truenegative , #falsenegative
Now, let's look at the four terms in another perspective and context: