'I came back because I have complete trust in the trainer's expertise and experience to provide exceptional training...' - Verified Student Review, Palo Alto Networks EDU-330 #paloaltonetworks #cybersecurity #cybersecurity training


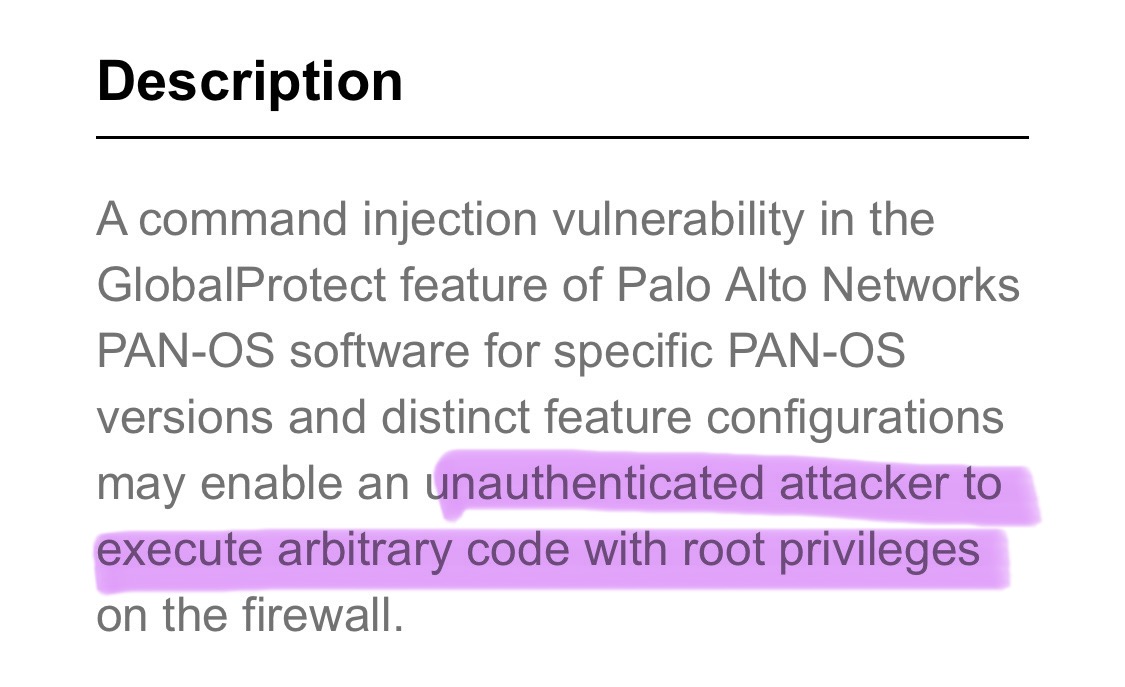
تفاصيل جديدة ومزيد من موشرات الاختراق لثغرة CVE-2024-3400 الخاصة بمنتجات paloaltonetworks
من هنا: paloaltonetworks.com/blog/2024/04/m…
#الامن_السيبراني



The XQL queries for hunting for known IoCs have been updated in our threat brief on #CVE20243400 : bit.ly/43YOECb







In this new case study, read how #channelpartners worked together to improve #paloaltonetworks skills across the ecosystem, lifting the levels of knowledge, skill and experience with Palo Alto Networks solutions and improving customer experience bit.ly/casestuds

2024-03-19 (Tuesday): #DarkGate infection from malicious Excel file. Since last week, DarkGate started using AutoHotkey script instead of AutoIt script for its infection. Indicators from an infection available at bit.ly/3vu8vfr
#Unit42ThreatIntel #TimelyThreatIntel




2024-03-26 (Tuesday) #Malvertising : Google ad leads to fake funds claim site, which leads to #Matanbuchus infection with #Danabot . Indicators available at bit.ly/49bCjeQ
#Unit42ThreatIntel #TimelyThreatIntel #Wireshark #InfectionAnalysis #Pcaps



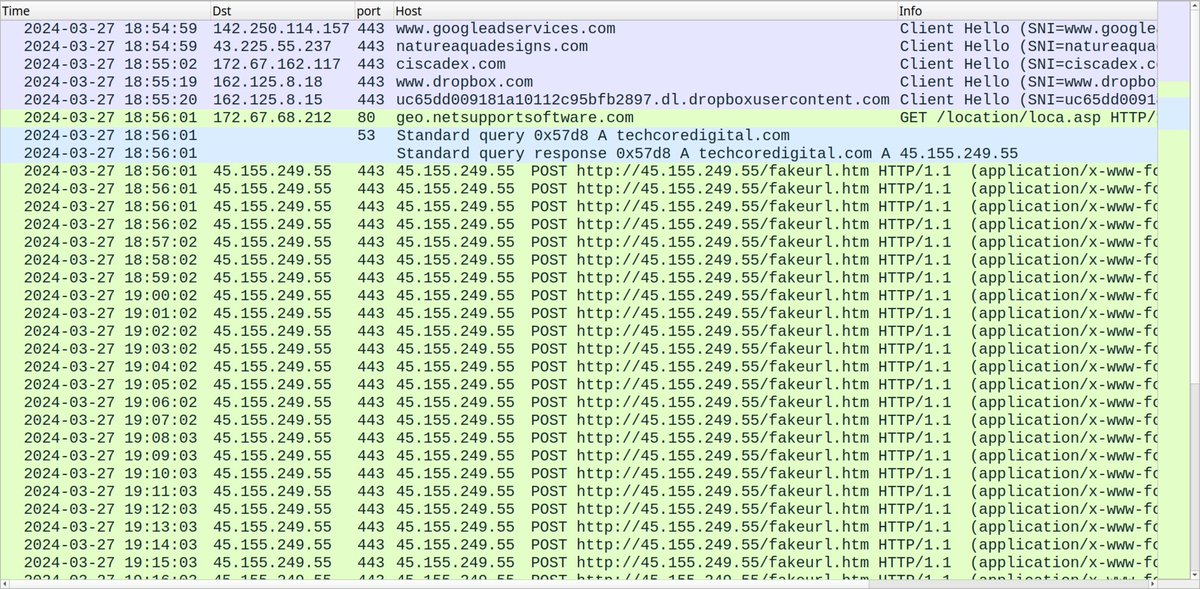
2024-03-27 (Wednesday): With the recent rise in malicious Google ads impersonating legitimate software, today we found one leading to a fake Cisco AnyConnect page pushing #NetSupportRAT . Indicators available at bit.ly/49mdPzG
#Unit42ThreatIntel #RemoteAccessTrojan

2024-04-04 (Thursday): We generated an infection in a lab environment based on the latest round of #KoiLoader / #KoiStealer activity. Initial bank-themed lures started earlier this week on 2024-04-02. Some indicators available at bit.ly/3PQut3r
#Unit42ThreatIntel


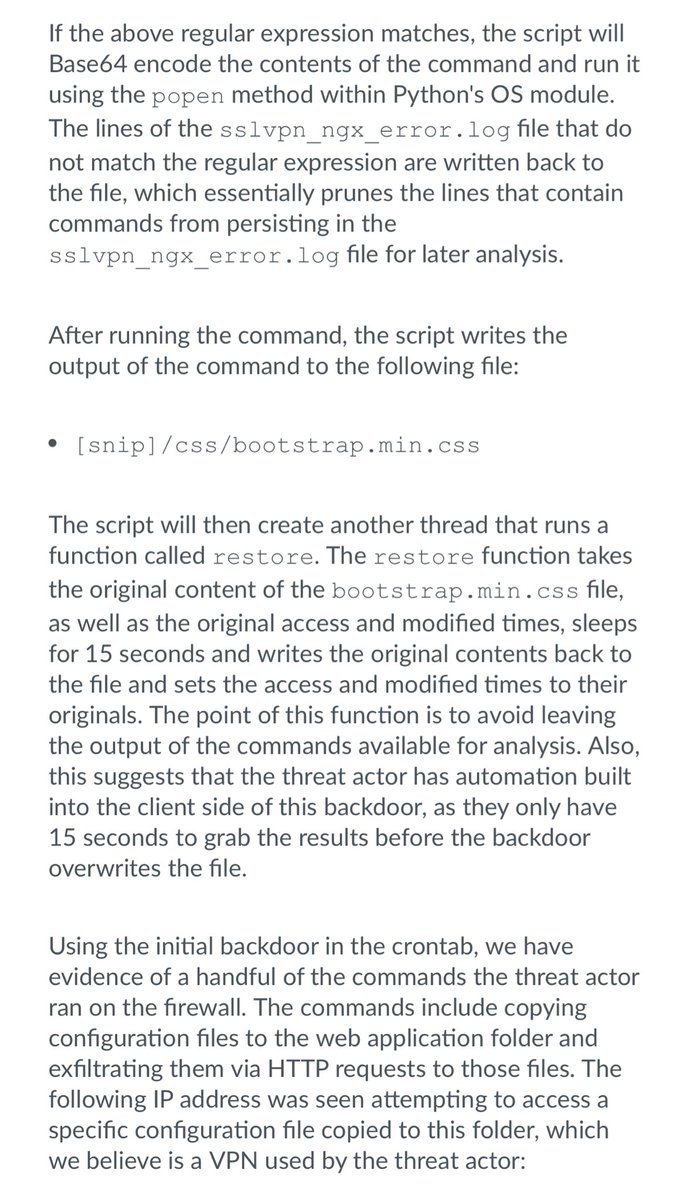
現在の攻撃スコープを改訂し脆弱性エクスプロイト試行レベルをレベル1〜3で評価しました。Operation MidnightEclipseから判明したアクティビティ詳細をUPSTYLEおよびCronjobバックドアのアクティビティで大幅改訂しました。 bit.ly/3JlnGLp #CVE2024300

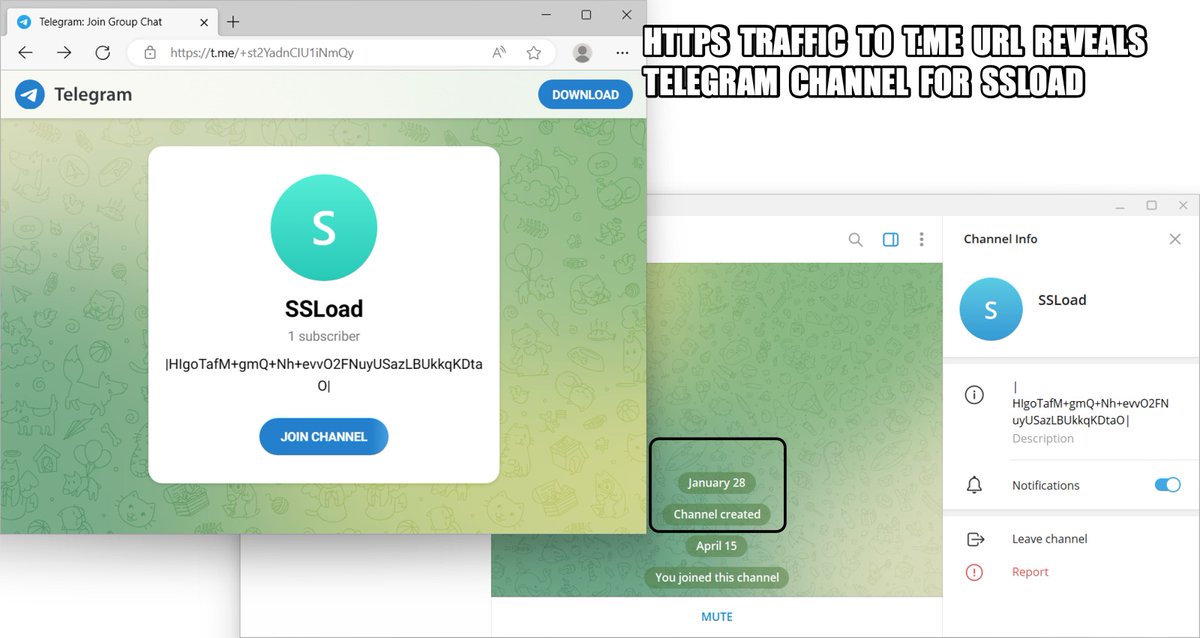
2024-04-15 (Monday): #ContactForms campaign pushing #SSLoad malware as early as Thursday, 2024-04-11. List of indicators available at bit.ly/49Cz1kL
#Wirshark #Unit42ThreatIntel #TimelyThreatIntel #InfectionTraffic