@SAPInsider #GRC2019 attendees... Just over 3 hours from now, we'll be teaming up with NextLabs for a live #demo . Come join us!
#accesscontrols #datasecurity


We are excited to announce that Citywide is expanding to the Cincinnati/Kentucky area. Please welcome Matt Hohman to the team !! 😁👏📲 #CitywideSolutions #security #videosurveillance #accesscontrols #intrusiondetection #parking #GateAutomation


#AWS #IAM security explained -
#cloudsecurity #CloudComputing #cybersecurity #infosec #AccessControls #IDENTITY #AccessManagement #riskmanagement #CISO #CICD #DevOps
CISO360
cybersecurity.att.com/blogs/labs-res…

#humanilluminance What’s your Hi? Educate motivate. Excel #cannabistechnologynetwork #telecommunications #internet #iot #accesscontrols #seedtosell #pos #tvmatrix #cabeling #led #cannawehelpyou #cannalight #likemindedalliance


Y’all don’t even know what this means…. but this is exactly why I am all in on #PRE 👀 Threshold Network ✜ 💎 #Crypto #ElectricVehicles $T #privacy #data #AccessControls #Threshold #proxyreencryption $NU $KEEP

Reminder from the Fed and Five Eyes: basic #cyberhygiene is essential. To fend off #cyberattacks , think #patchmanagement , #MFA , and user #accesscontrols .
#cybersecurity #cybersecurity consultant #securitytips
cybersecuritydive.com/news/feds-thre…


Thales 𝙲𝚑𝚛𝚒𝚜 𝙾𝚕𝚒𝚟𝚎 is presenting “What’s ahead for 2018?” today at the CDM Media #CISO Summit in Dallas #DataSecurity #Cloud #AccessControls #Regulations #Governance

🌟 Safeguard your sensitive data across multiple clouds with #OasisDefender 's robust encryption and access controls. 🌐🔒
#DataSecurity #Encryption #AccessControls #Compliance #SecureCloud #OpenAI #Cybersecurity #CloudSecurity #AI #Software #innovation #MachineLearning #Robotics

End employee time theft today! Let every time count. Contact us for real-time Access Control and Attendance Systems.
#MarginsToGo
#AccessControls
#BuyMargins


Did you know that we install full height turnstiles?! A turnstile is a form of gate which allows one person to pass at a time. Turnstiles are mostly used for two reasons: security and safety.📲👏😁 #turnstiles #security #citywidesolutions #accesscontrols #intrusiondetection


Another successful install in Central Ohio. Citywide Solutions utilized Automatic System’s smart lane turnstile technology to allow comfortable access to pedestrians while maintaining ADA compliance. #citywide #Columbus #accesscontrols #security #automaticsystems

The #Cloud Security Race. Are you pacing yourself to go the distance? #Cloud #DataSecurity #EndpointSecurity #AccessControls Via @Gemalto Cc @evankirstel


With Privacera, users can implement fine-grained #accesscontrols to better protect sensitive #data . #clouddata #governance
Learn more about our #ApacheRanger plugin and how to control policies at different levels in this blog: hubs.ly/H0TJTnk0


Tune in to FS1 at 10:00 AM to catch Kaulig Racing Matt Kaulig and AJ Allmendinger in their practice run for the EchoPark Grand Prix. Let's go #TrophyHunting !
#EveryPartForEveryDoor #NASCAR #garagedoors #garagedoorrepair #garagegoals #accesscontrols #garagedoors eals


Learn #ZeroTrustSecurity with
Dr. Abhilasha Vyas, session on Conditional #AccessPolicies .
Get insights into safeguarding your organization's data with advanced #accesscontrols
Date: 25th November 2023, 10.25AM IST
RSVP: null.community/events/946-ahm…
null - The Open Security Community #nullahm #cybersecurity


Working from home presents unique challenges for security teams. Is permissions and access controls the answer? bit.ly/2WsQx8A
#WorkFromHome #Compliance #datasecurity #CyberSecurity #infosec #cyberthreats #RemoteWorking #VPN #AccessControls #Permissions #Covid_19

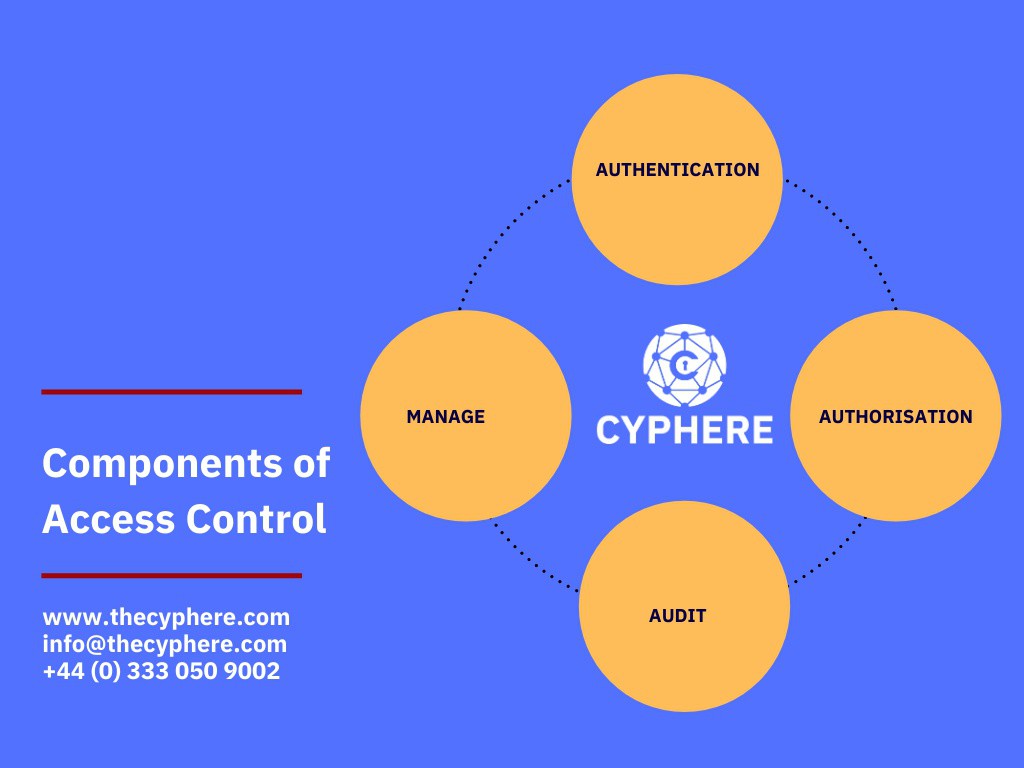
Access control security measures include access control lists, commonly written as ACLs to maintain the integrity of a network or an environment.
Read more 👉 lttr.ai/eYFk
#dataprotection #AccessControls #Informationsecurity