




Nice explanation from #dzone on SSL Offloading and how it works bit.ly/2thdZtW #ssl #dataintransit #encryption #devsecops #webprotection #SSLterminationvsbridging lnkd.in/g4ACWPc

Machen Sie #Datenaustausch und #Datenspeicherung in Ihrem Unternehmen sicher(er): Mit dem „Helden-Paket“ von @Cryptshare und #digitronic → Hier mehr erfahren &📢10% Aktionsrabatt sichern: buff.ly/3u1h5xo
#Verschlüsselung #DataAtRest #DataInTransit #360GradSchutz


More organizations are #encrypting data than ever. What's driving adoption for protecting #DataAtRest and #DataInTransit ? TLS #GDPR tek.io/2LeWmCK

We are living in a world where data security is crucial. Our latest blog talks about 'Encryption: Data in Transit vs Data at Rest'. Check it out now: bit.ly/3y8oYCz
#DataEncryption #DataInTransit #DataAtRest


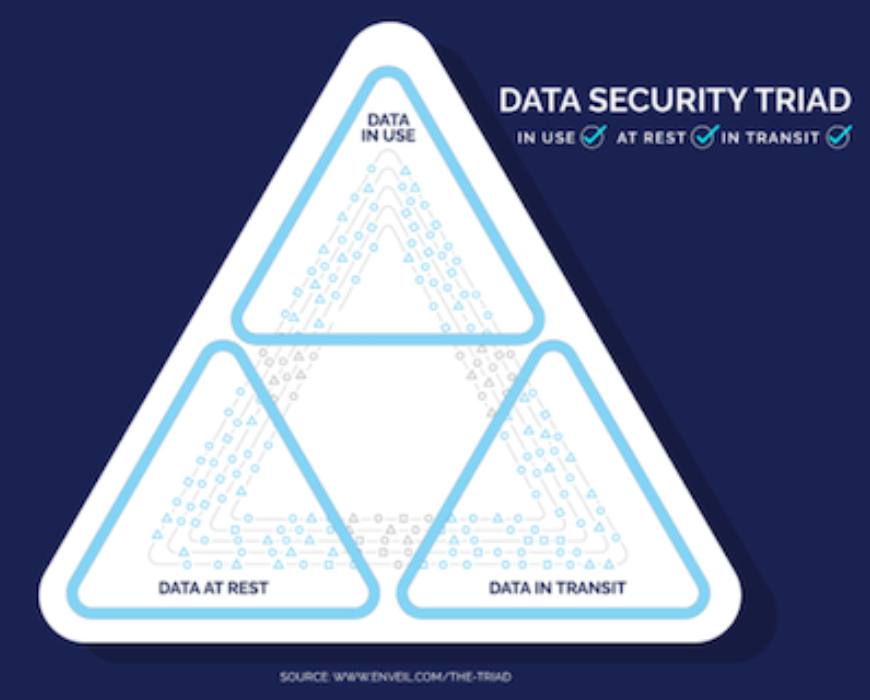
Uncovering The #DataSecurity Triad - bit.ly/2Uil2Or-Ttx Ellison Anne SecurityWeek
➡️
#CyberCrime
#Organizations
#Enterprises
#CyberRisks
#DataAtRest
#DataInTransit
#DataInUse
#Encryption
#CyberThreats
#InfoSec
#CyberAttacks
#DataBreaches
#CyberSecurity
#DataExfiltration


Get ahead of data-in-motion risks with a platform that understands lineage and alerts you to unauthorized data exposure in real time.
#datasecurity #cloudsecurity #datainmotion #dataintransit #sensitivedata #datalineage #infosec #clouddata social.normalyze.ai/u/aQpBek


The race is over. KnectIQ has #datalossprotection that eliminates the foundational #threat to #PKI - no #publickey for #dataintransit . #encryption #quantumcomputing #qkd #datacentric #zerotrust lnkd.in/ejiMj9a

We understand the importance of protecting patient healthcare data. Our technology leverages traditional encryption security and an advanced layer of obfuscation defense. As a healthcare provider, you should not have to worry about your data-in-transit security.
#dataintransit


How do you ensure that the files you share with external parties remain secure during and after the transfer? Read our latest article on potential threats when sharing data or files: zcu.io/qCp1
#dataintransit #filesharingservices #storagesecurity #MyPrivacyGmbH

#cloud based #cybersecurity technology that prevents the use of valid #credentials by #hackers while delivering #world -class #dataintransit protection is the next step in #datalossprotection . KnectIQ solves. @SolarWinds Microsoft lnkd.in/eYxi-W6


Major Singapore Bank Completes First DLT Trade Financing Transaction #singapore #cimb #blockchain #internetofthings #dataintransit #bitsmart bitsmart.io/bitcoin/news/m…

#Encryption is the process of #encoding a message or #information in such a way that only #authorized parties can access it and those who are not authorized cannot.
#message #DataAtRest #DataInTransit #protectInformation #cryptography #unreadable
ssd.eff.org/en/module/what…

Rather than chasing the threat of the day, DataStealth protects all of your sensitive data whether at rest or in transit. Let's Talk #DataProtection #DataInTransit #DataAtRest #DataStealth


