
Prevent #securitybreaches by detecting vulnerabilities in a click. #ZeroThreat is a super-friendly #securitytesting tool with an AI-powered crawler.
Check out more benefits of it at zerothreat.ai
#CyberSecurity #infosecurity #DataSecurity #SecurityInsights

Do you know that cybersecurity breaches are on a rise? Most of these incidents happen due to human error.
#WeAreExponential #10xDS #NXSecure #Cybersecurity #CyberAttacks #CyberThreats #SecurityBreaches


An Information Security Management System offers the following: . . . #trojanhuntindia #InformationSecurity #ISMS #SecurityManagement #Protection #Compliance #Standards #Regulations #RiskManagement #BusinessContinuity #SecurityBreaches #Penalties #CyberSecurity


Stay informed about the recent security breaches as HTX resumes withdrawals. Are other platforms taking action? Stay vigilant! #SecurityBreaches #HTX #StayInformed


#Cybercrime is any #crime that takes #place #primarily #online . #Cybercriminals often #commit #crime s by #targeting #computer #networks or #devices . #Cybercrime s can #range from #securitybreaches to #identity #theft . wp.me/p3ARH8-1so

FBI recommends passphrases over complex passwords
ow.ly/IYbo50ytffA
To learn more about Cyber Security, sign up for our series:
techworksgaston.com/cybersecurity-…
#cybersecurity #informationsecurity #Securitybreaches #gastoncounty

What are the signs of an IT security breach?
☠️ Sudden increase in pop-ups and spam.
☠️ Frequent error messages.
☠️ Anti-malware software sends more alerts.
#DigitalFire #ITSecurity #Cybersecurity #RemoteWork #SecurityBreaches



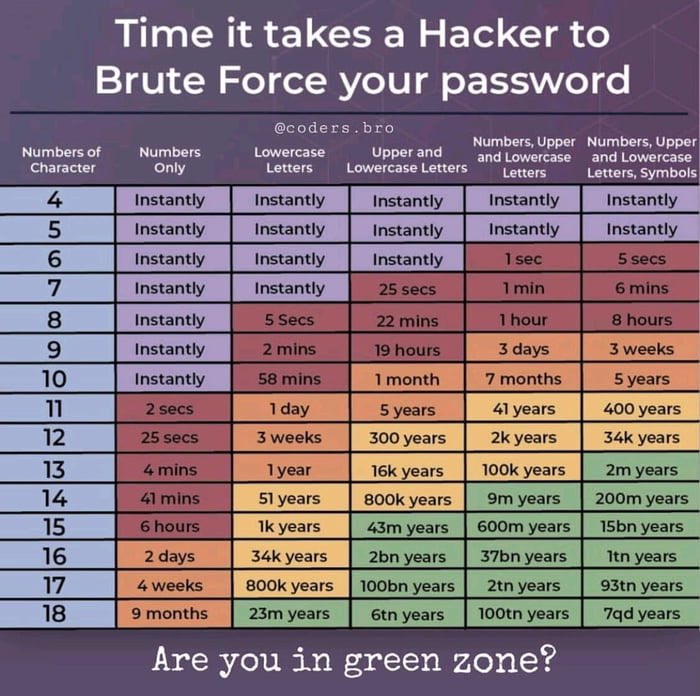
Up to 95% of #securitybreaches are due to human error. Make sure your #password is strong enough to withstand #hackers . Take a look over this password sheet and see if it’s time to change your passwords.
#Cybersecurity Source: @ coders.bro

Prevent #securitybreaches by fixing misconfigurations in the cloud deployments through our reliable #cloud security services.
Write to us: [email protected] or visit at tataadvancedsystems.com/cybersecurity.…
#cybersecurity #dataprotection #cloud #CloudServices #DataSecurity


According to SC Media, 93% of businesses have undergone #CloudMigration . Embracing cloud migration presents unique #SecurityChallenges that require adopting integrated #SecuritySolutions in order to protect sensitive data and prevent #SecurityBreaches . scmagazine.com/resource/how-c…

Does data breach worry you alot?
Say no more!
NITA-Uganda @CymbellAdvocat1
#DataSecurity #securitybreaches #cymbelladvocates #NITA


Cyber Attack trends 2019 Mid-Year Report.
#cyberattacks #cybersecurity #securityandrisk #securitybreaches #cybercrimes #hackers #cybersecurity predictions #cybersecurity week #ransomeware #securityintelligence #ImpactQA
research.checkpoint.com/2019/cyber-att…


Lynda Bennett is joined by fellow LS partner Mary Hildebrand & @McGill_Partners’ David Anderson to discuss what regulators are doing to incentivize companies to avoid #SecurityBreaches in today's episode of “Don’t Take No for an Answer.' bit.ly/33vo60y #cybersecurity

What is the DDoS Attack and #Howto Effectively Resist It? bit.ly/DDoS-Attack
#DDoS #DDoS Attack #CyberAttack #DDoS threat #NetworkSecurity #DDoS Protection #StopDDoSAttack #cybercriminalattacks #cybersecurity #businesssecurity #websitesecurity #security breaches #security #Tips

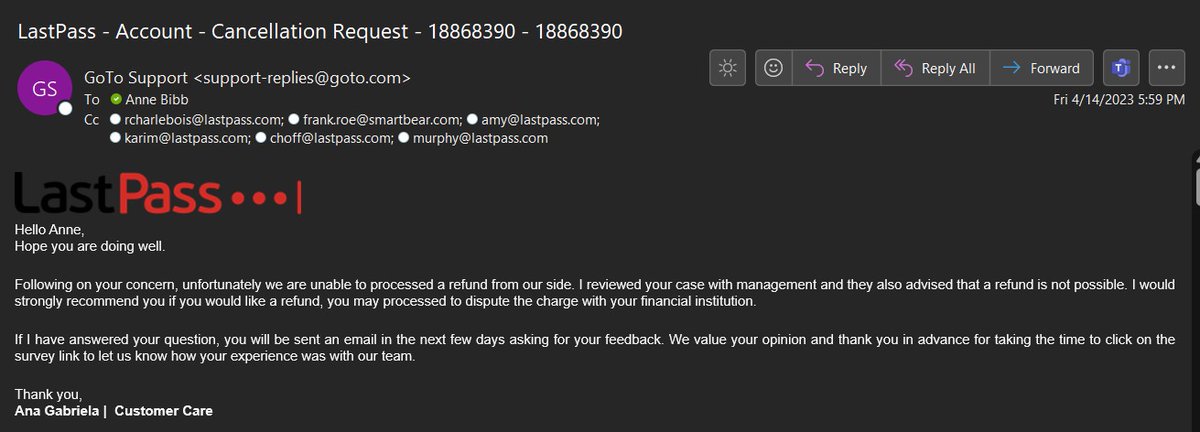
PSA to anyone using LastPass - BEWARE!
4 months and still no resolution. LastPass neglects customers and their concerns. Your data and money are at risk. RUN.
#SecurityBreaches #BadCustomerService #ProtectYourData #ProtectYourMoney #DitchLastPass #CyberSecurity

Did you know insiders are responsible for 75% of all #securitybreaches ?
Join us at our next CISO Corner to learn proven risk management strategies for preventing and mitigating insider threats. Register now:
bddy.me/3iQzr0d

🛡️ Explore our latest blog 📖, where we outline the 10 critical questions you must ask about #dataprivacy .
(Link in threads)
#databreaches #datasecurity #dataprotection #securitybreaches #cybersecurity #webappfirewall #waap #apptrana #indusface


The coming year looks promising on many levels. However, there could also be an inordinate rise of #securitybreaches and #attacks .
Confused? Learn more about the 8 frightening predictions about #Cybersecurity in 2020: buff.ly/2EPSjqZ
#DataProtection #DataSecurity



